''There’s no question that it has become harder to maintain standards in one key area: cybersecurity. As millions have transitioned to working from home, the strain on computer networks has soared, presenting vulnerabilities to hacking. And ransomware attacks and other cybercrimes are on the rise during the pandemic. ''- Europol.
The global shift to remote has been challenging for most businesses and placed a considerable strain on security teams. What are the major cybersecurity risks? What preventive measures to take to avert them? And how to find a secure software development partner in this new reality?
Here are the answers to these and many other questions.
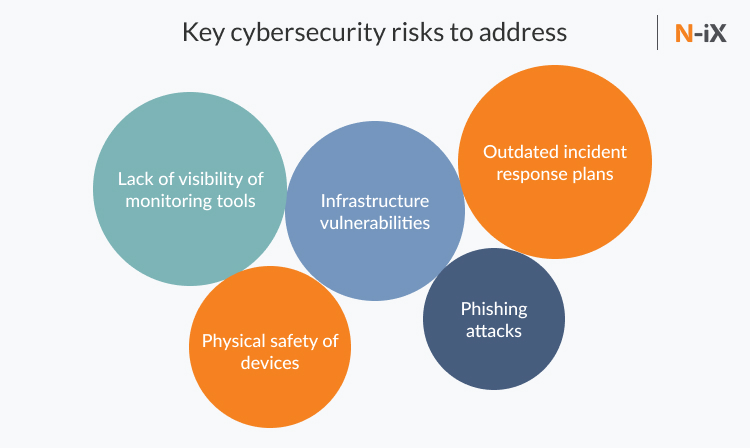
Key cybersecurity risks for software development companies in the time of remote
As a result of the COVID-19 outbreak, companies were forced to switch to remote work on short notice. Here are the key cybersecurity issues that needed to be addressed promptly, effectively, and proactively.
-
Infrastructure vulnerabilities
To prevent any risks associated with remote infrastructure, cybersecurity teams needed to perform endpoint hygiene, connectivity performance checks on all corporate machines, and running VPN load tests to spot potential cybersecurity risks and address them proactively on the company level.
For instance, N-iX, an Eastern European software development provider, has performed such a VPN load test with 30% of employees to ensure that corporate VPN is secure in a time of remote work.
Also, working on personal laptops and using personal programs or shadow IT may give criminals access to the company's resources and systems, which may lead to disclosure, theft, modification and corporate data losses. Therefore, using personal devices is not to be allowed.
At N-iX, all employees were provided with corporate laptops when they joined the company. Therefore, when we switched to the remote work mode, everybody had a secure, encrypted device to work with.
-
Lack of visibility of monitoring tools
To ensure that monitoring tools provide maximum visibility, the company needs to pay close attention to the internal security monitoring capabilities and log management to maintain security when employees work remotely. We will view log management in more detail later in the article.
-
Outdated incident response plans
Due to the changed work environment, incident response plans and protocols also need to be adjusted to the current threats. Today even typical and well-managed cybersecurity risks can become more severe if the team can’t respond effectively.
To ensure remote work cybersecurity, it is vital to make sure that the cybersecurity team has access to the equipment they need to be effective. What’s more - all documentation also has to be updated with particular attention to problem areas, such as system logs, VPN, etc.
-
Physical safety of devices
Data loss prevention is one of the main tasks of security professionals. As far as remote work cybersecurity is concerned, there is a risk of the physical safety of devices. A lost or stolen device poses a peril of data loss.
To mitigate this cybersecurity risk, all company laptops have to be encrypted by default and the encryption of personal devices should be checked in accordance with BYOD (bring your own device) policy. However, BYOD is allowed when it is absolutely required and should be approved by the line manager.
-
Phishing attacks
Phishing attacks are cyber-attacks that use disguised email as a weapon to get confidential information such as passwords. The attackers masquerade as a trusted entity, so employees must be informed about the ways to spot fraudulent behaviour.
This cybersecurity risk is mitigated by appropriate awareness education on a company level.
For instance, N-iX conducts regular phishing attack scenarios to mitigate the risk of accidental sharing credentials.
How to ensure secure software development in the time of remote?
In order to effectively respond to all security threats and prevent potential risks, the company needs to have a well-established security policy, a solid Business Continuity Management Plan that covers different possible scenarios (including the pandemic and shift to remote work on a company level), comply with international security regulations, and undergo regular internal and external security audits.
Here are the security controls that allowed us to transition to remote work smoothly, without any risks, and without interrupting our operations or services that we provide to our clients.
Compliance with Infosecurity regulations and standards
Compliance with international regulations and security standards is vital to ensure remote work cybersecurity.

There are key international infosecurity standards and other regulations a reliable software development company must be compliant with.
Compliance with ISO 27001 means implementation of administrative and physical controls to ensure confidentiality, integrity, and availability of information assets.
PCI DSS compliance is obligatory for a company that accepts card payments and stores, processes and transmits cardholder data.
Compliance with HIPAA law is required when working with medical data.
To comply with international security standards, IT companies undergo regular audits, both internal and external ones. Reliable outsourcing vendors cooperate with authorised third parties to perform regular cybersecurity assessments. For instance, Bureau Veritas runs audits for ISO 27001:2013 and ISO 9001:2015 audits for N-iX.
What’s more, the N-iX Information Security team conducts internal audits of information security and projects twice a year to ensure compliance with internal information security policies and project requirements.
Also, the N-iX Information Security team runs a quarterly internal review of PCI DSS controls, according to the requirements of PCI DSS standards. In addition, there is an annual external audit of the compliance with PCI DSS requirements.
Moreover, N-iX has developed policies for the protection of personal data and healthcare data. The Information Security team runs technical and organizational controls to ensure that projects are compliant with GDPR and HIPAA requirements.
Business Continuity and Disaster Recovery Plan
To ensure continuity of network, infrastructure and resources, companies need to have a Business Continuity and Disaster Recovery Plan (BCP) in place. The plan covers scenarios for the recovery of critical business functions and business operations in case of force majeure situations, natural disasters, human-made, community, and medical disaster scenarios, etc.
Also, the information security team should conduct risk assessments of all information assets and resources and develop a risk management plan to reduce and minimize the identified risks.
Long before the pandemic, N-iX developed a business continuity plan, according to which all company employees must have the technical ability to work remotely.
N-iX Business Continuity and Disaster Recovery Plan covers:
- Test scenarios for infrastructure, network, and physical security;
- Load VPN tests;
- Network security attacks;
- Power failures;
- Server failures;
- Backup scenario;
- Backup failure, etc.
All corporate devices are encrypted. After five minutes of inactivity, work machines are automatically locked. Also, antivirus software is installed on all users’ workstations.
According to the corporate password policy, the user’s account is blocked after several unsuccessful login attempts. Access to the N-iX network and resources is monitored and logged, including the access via VPN.
Secured remote access to the office infrastructure is provided via SSL-based VPN and two-factor authentication.
Our IT security incidents response policy allows us to manage and eliminate detected information security incidents.
What’s more, to ensure annual training for information security personnel, the company switched to online training on information security and GDPR.
How to maintain remote infrastructure security
Make sure you and your software development partner take the necessary measures to maintain infrastructure security when working remotely.
-
Sustaining all critical logs in a SIEM
SIEM or security information and event management is a software aimed at maintaining security within the organization by collecting the data on the authentication to the business systems. It is of utmost importance to track the logs to the critical sources, especially in a time of remote work as disruptions in the way people access information may trigger an increase in undesired activities, thus posing cybersecurity risks.
To prevent that, you have to understand how logs look like if the infrastructure is secure. That, in turn, will make detecting the disruptions in the system way easier and ensure secure software development.
The critical logs to collect are:
- VPN logs;
- Administrator logs, e.g. new accounts creation, changes to account permissions, etc.;
- Access logs for business systems.
Collecting logs will ensure more visibility into how secure your infrastructure is and help mitigate cybersecurity risks.
-
VPN with posture checks and zero-trust access
VPN is not something new for the outsourcing vendors, as it is a common practice to secure access to companies’ networks. However, the work from home mode has brought VPN usage to the next level.
Securing remote access is as critical for IT outsourcing companies as probably never before. The way to advance the VPN design is posture checks, or, simply put, validation of the connecting endpoint before allowing authentication. Posture check helps you understand the security status of the endpoint, thus eliminating the unwanted insecure access to your system. Moreover, posture checks become of particular importance if the remote developers need access to your infrastructure to perform their tasks.
Another vital aspect of mitigating cybersecurity risks for businesses is zero-trust network access. This means that employees have access only to the information that is critical for their task performance. So, a specific specialist gets specific access for a limited period of time.
-
Using privileged access management tools
Privileged Access Management tools (PAM) are aimed at managing access to critical information in the company, thus ensuring remote software development security. They are important as excessive access increases the risk of exposure. Also, PAM tools limit the time of given access to the minimum needed to perform a task, thus helping to eliminate risks and ensure secure software development.
In terms of IT outsourcing, PAM ensures that all accounts are only used for the intended purpose and when it is required. For remote work cybersecurity, privileged access management tools also provide the right permissions for access via Virtual Desktop Solutions or a Remote Desktop Protocol.
-
Endpoint Detection and Response
EDR or Endpoint Detection and Response tool is used to ensure understanding what is happening on each endpoint, thus helping to detect and prevent the cybersecurity risks. EDR is commonly used by organisations outsourcing their services.
Here are some examples of use cases for Endpoint Detection and Response:
- Monitoring processes, registry changes, file and network activity;
- Preventing unwanted software installation;
- Hunting for file hashes, processes and registry settings, etc.;
- Isolating endpoints from the network in critical situations;
- Eliminating applications that represent cybersecurity risks.
-
Cloud security posture management
There is a popular misconception that moving data to the cloud equals sacrificing security. Although it is not true anymore, the cloud poses a number of cybersecurity risks. To know more about the cloud cybersecurity risks for businesses and ways to tackle them - read the article.
One of the ways to address possible cloud-related cybersecurity threats is cloud security posture management- a technology that enables visualising, monitoring, alerting and reporting on configuration status and changes in cloud environments, e.g. AWS, Google Cloud and Azure.
What’s more, this technology alerts on misconfigurations or unexpected changes introduced by outsourcing partners, so you can quickly remediate to remove the risk presented.
-
Cloud Access Security Broker
Cloud Access Security Broker or CASB is a technology that enables businesses to monitor what is happening within their core SaaS business applications such as Office365, Salesforce, Slack, etc. In the case of detecting uncommon behaviour in the app, this technology alerts you, thus helping to prevent remote working cybersecurity risks.
To enable monitoring and alerting, you need to integrate your SaaS business applications with the APIs. CASB solutions can also run discovery tasks to reveal if your SaaS applications contain any sensitive data as classified by Azure IP, Titus, Boldon James, etc. From a compliance point of view, it can help present reports to prove that no sensitive files reside in the SaaS.
This technology becomes of even greater importance if you cooperate with an outsourcing vendor.

How to choose a secure software development partner?
If you outsource your software development, you have to make sure that your outsourcing vendor follows the corresponding procedures and policies to meet your cybersecurity demands and ensure secure software development.
- The company complies with international infosecurity regulations, has all the necessary security controls in place, and a solid Business Continuity Management Plan it adheres to.
- The outsourcing vendor undertakes recurrent internal audits of its compliance with the security standards and policies. Also, the compliance must be regularly verified by an accredited third party.
- The company has a strict policy concerning password security (e.g, demands for strong passwords, quarterly password resetting, etc.)
- The IT company can provide an accurate information asset inventory and indicate what networks it will use to store, access, and transfer the data. The company must also define what controls they will apply to ensure the integrity, availability, and confidentiality of the information.
- There is a contract clause that states what happens to the data when the agreement is terminated. An outsourcing provider has to confirm in a written form that the data has been deleted or transferred back to its owner.
- The IT company can provide pseudonymization of the data to ensure data protection and compliance with GDPR. Pseudonymization is a process when personal data is replaced by artificial identifiers (pseudonyms), and thus the IT vendor has no access to actual users’ personal data.
Why choose N-iX as your software development partner?
- N-iX is compliant with ISO 27001:2013, PCI DSS, ISO 9001:2015, GDPR and HIPAA. The company undergoes annual external security audits as well as internal audits two times a year to ensure maximum security;
- We provide protection for intellectual property according to the legislative and contractual agreements. Our information security teams regularly review cybersecurity policies to guarantee they are suitable, adequate and efficient.
- N-iX provides secure log-on procedures, password and cryptographic keys management, network security, as well as information asset management.
- N-iX network vulnerability scan is performed monthly, access to the N-iX network and resources are monitored and logged, including user access to resources through VPN.
- To guarantee annual training for information security personnel, the company has introduced online information security training.



