The brave people of Ukraine are defending their freedom from the atrocious russian invasion on multiple fronts. As a country with one of Europe's largest IT industries, it is unsurprising that cybersecurity has become one of the crucial lines of defense. Therefore, let’s take a closer look at the current state of local information security and the best practices that local technology companies use to ensure data security in Ukraine.
Ukrainian cybersecurity receives internal and global support
The number of russian-sourced malicious attacks that was steadily growing in the months leading up to the invasion had reached its peak in the first 48 hours. The Ukrainian military, governmental, and infrastructural institutions experienced a reported surge of 800% in various cyberattacks. These attacks, though still persisting, are being effectively countered by the mitigation efforts from the Ukrainian side.
In addition, government institutions that are responsible for cybersecurity in Ukraine have received strong support from numerous volunteers who work in the Ukrainian tech industry. The Ukrainian government welcomed their help by issuing a decree that authorized these volunteers to test and look for vulnerabilities in various critical informational systems. Many of our experts at N-iX have also joined the ranks of volunteers and are participating in various projects that improve data security in Ukraine. For example, our engineers helped develop, test, and implement DDoS protection for a resource that records all infrastructural damage caused by the russian occupants.
Cybersecurity in Ukraine has received support from the outside as well. For example, the EU has mobilized a team of cybersecurity experts from six different countries to counter the cybersecurity threats in Ukraine. Furthermore, the collective efforts of Lviv IT Cluster, N-iX, and several other tech companies helped Ukraine obtain over 5,000 Starlink satellite internet terminals from Elon Musk’s SpaceX and USAID. Ukrainian experts have been very impressed with these terminals that provide reliable backup for times when conventional internet connection fails. As a result, even though occasional outages do occur in the affected territories, the majority of the Ukrainian cities are able to maintain a stable connection to the web.
All in all, the cybersecurity in Ukraine remains strong. While hacking groups still perform occasional malicious attacks on Ukrainian institutions and even regular citizens, the combined efforts of Ukrainian authorities and the volunteers from the IT industry have managed to build a solid line of cyber defense.
Ukrainian IT companies maintain high levels of delivery
The IT sector is the largest export service industry in Ukraine responsible for over 4% of Ukrainian GDP and is therefore extremely important to the country’s economy. While there were concerns that tech companies would be one of the targets for malicious activity, the industry itself remained relatively unaffected.
After the first signs that the russian invasion was imminent, Ukrainian tech companies took the time to prepare for all possible scenarios, and, when it actually began, were able to quickly adapt to new realities. Various measures were taken to maintain the high level of delivery, including employee relocation to safe development hubs in Western Ukraine such as Lviv, as well as the opening of new development centers in Poland and other neighboring countries.
This has allowed the Ukrainian tech companies to avoid setbacks in cooperation with their clients. By the third week of the invasion (~10-11 March), a survey from DOU, the leading Ukrainian IT job portal, found that 80-90% of Ukrainian IT experts had returned to their normal work mode. Since then, this number has been gradually increasing.
Furthermore, while the uncertainty caused by the invasion led to a significant drop in the number of open vacancies in the first weeks of the invasion, it has since grown dramatically. Indeed, by the end of March, both open and filled positions in the Ukrainian IT market reached higher numbers than in the months leading up to the war.
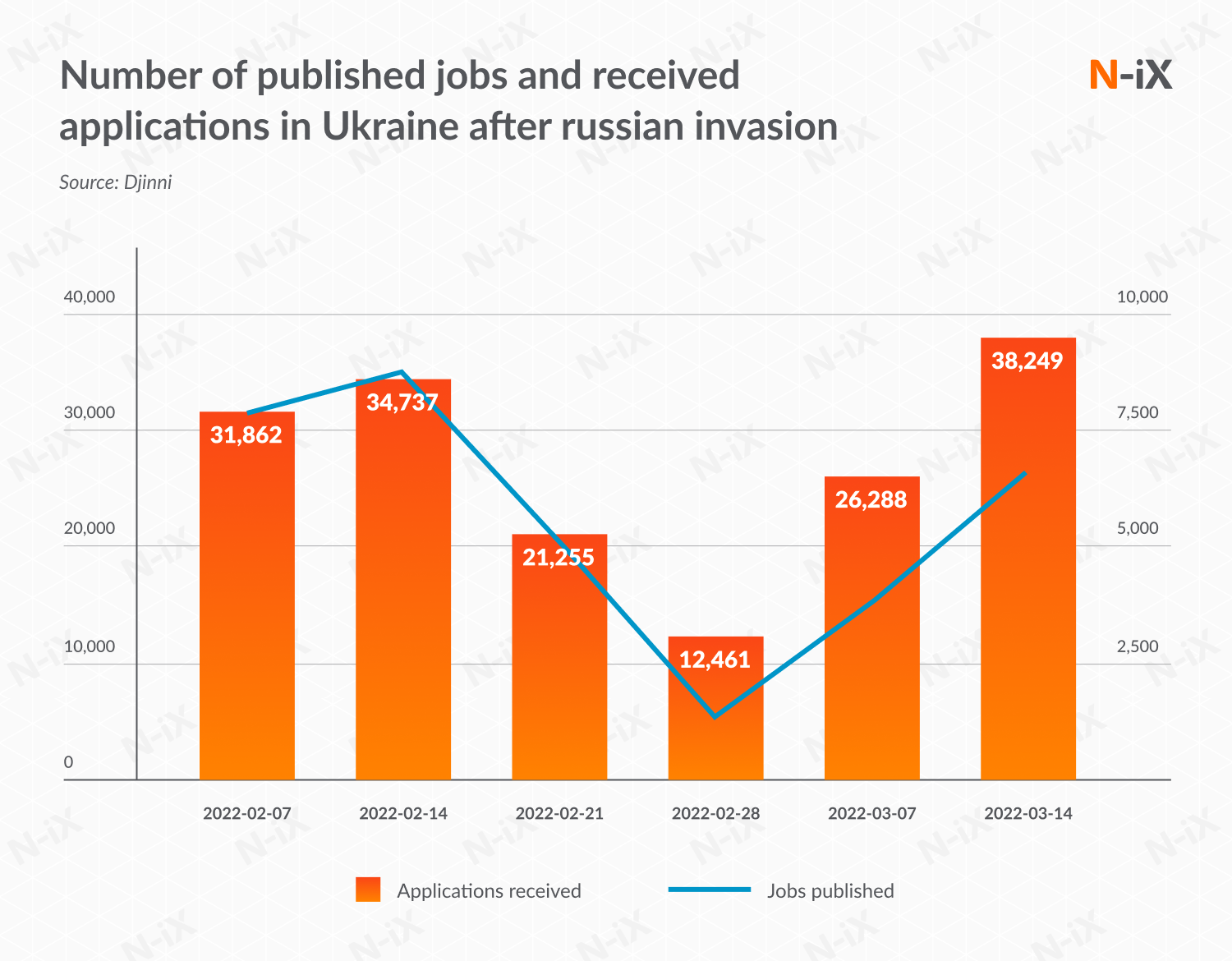
Moreover, local tech companies not only manage to keep the quality of delivered services but are also maintaining strong cooperation with their clients. A survey conducted in the middle of April by DOU has found that 44% of all Ukrainian IT companies have retained 80%+ of all of their contracts, while 37% have not lost a single one and continue working with all of their clients.
How N-iX deals with cybersecurity threats in Ukraine
N-iX has partnered with many enterprises that operate in highly data-sensitive industries such as finance, healthcare, and energy, and it is extremely important for us to ensure that customers’ data remains protected. Hence, in addition to the already established high standards of information security, the N-iX security team created new measures that bolstered our cybersecurity even further. Let’s take a closer look at how N-iX deals with cyberthreats.
1. Compliance with data security standards
One of the key fundamentals that ensure safe access and use of data in a tech partnership is compliance with data protection standards. To make sure that our company meets all contractual, legal, and regulatory requirements, N-iX complies with the following data protection standards:
- ISO 27001:2013. This standard ensures that a company establishes secure management systems for their clients.
- ISO 9001:2015. The standard signifies a high level of organizational management.
- PCI DSS. This is an obligatory standard that ensures the financial data security of companies that accept card payments and handle cardholder information.
- GDPR. Compliance with this EU regulation ensures data protection and privacy on the territory of the European Union.
- HIPAA. This standard ensures the secure handling of sensitive medical data of our clients that operate in healthcare.

To make sure that N-iX meets these standards, we go through regular external audits by third-party service providers. In addition to external audits, the N-iX Security Team performs regular internal audits (twice per year, on average) to make sure that our organization and all employees remain updated on the latest developments in data protection.
2. Business continuity plan (BCP)
The N-iX Security Team has implemented a robust business continuity and disaster recovery plan that ensures the smooth operation of all critical business systems during force majeure events, war being one of them. The N-iX BCP covers the following:
- Backup scenario;
- Backup failure;
- Server failures;
- Power failures;
- Network security attacks;
- Scenarios for testing physical, network, and infrastructure security.
Moreover, this plan is being constantly improved and updated to cover all potential and newly-discovered vulnerabilities. Indeed, in the months leading to the invasion, we have updated our BCP to incorporate and prepare for all possible scenarios. Even before the attack, we encouraged our colleagues to relocate to Western Ukraine or Poland and offered relocation bonuses. In the first weeks of the war, over 500 of our specialists evacuated from the affected territories to safety (either to Western Ukraine or the newly opened development center in Poland). Thus we were able to keep the service delivery level above 95%.
3. Utilizing the benefits of the cloud
N-iX began actively utilizing the cybersecurity capabilities of the cloud long before the war. Ever since the Covid pandemic broke out and working remotely became the new standard, we have been actively moving critical internal systems to the cloud to allow our employees to work safely from anywhere. This proved to be invaluable in the current circumstances as we had to close several local development hubs and relocate our employees to safety.
All leading cloud providers such as Azure, AWS, and GCP are constantly working on improving the security of their solutions. Moreover, they cooperate closely with their official Ukrainian partners like N-iX to help counter cybersecurity threats in Ukraine.

4. Additional security measures
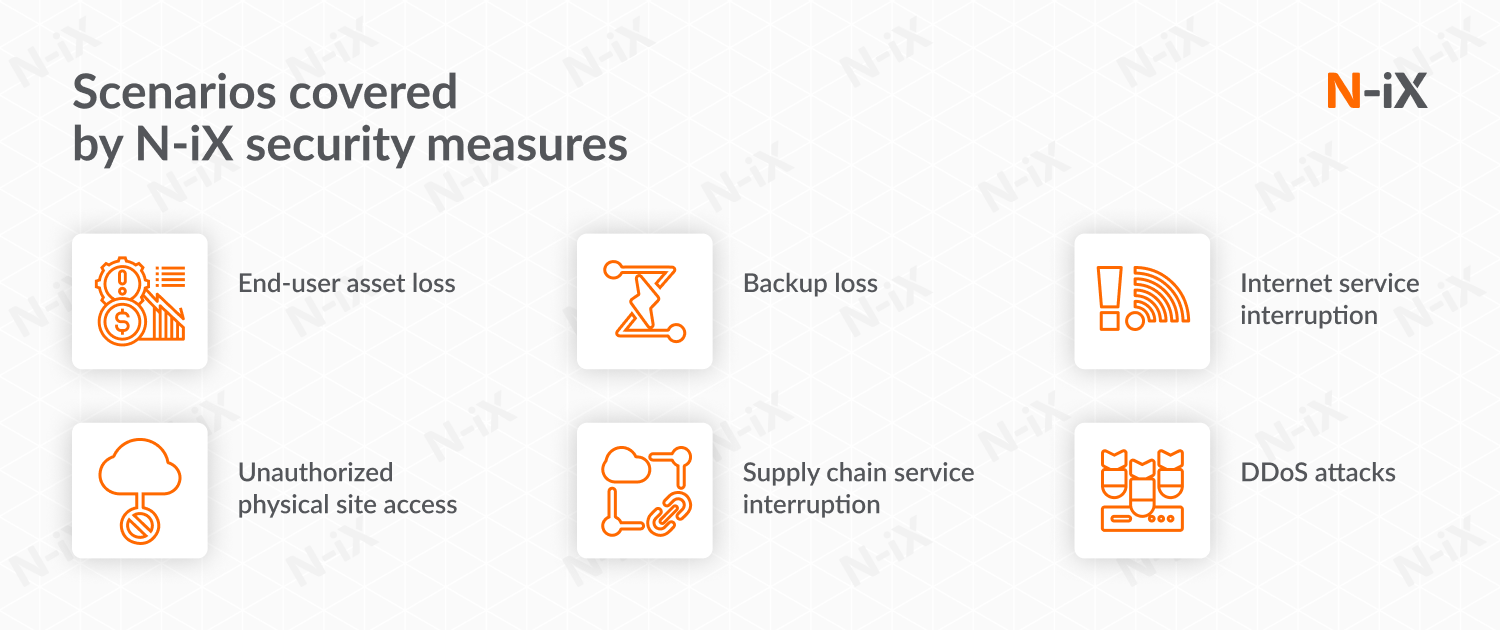
As the invasion of Ukraine was becoming more and more apparent, our infosec experts incorporated additional measures that would prepare the company for these events. These measures, combined with already established information security practices, cover various scenarios that could lead to vulnerabilities and ensure that all data remains protected in any circumstances. The following scenarios are covered:
- End-user asset loss. We encrypt all of our devices and invoke remote wipe procedures as soon as a device is lost.
- Unauthorized access to physical sites. The premises of our development centers in Lviv are guarded 24/7; an emergency sanitation procedure has been invoked in our development center in Kyiv, with all servers (except CCTV) deleted and all VPN links moved down; Dot1x authentication is implemented on all on-premise networks.
- Backup loss. We store all backups in two separate locations in Lviv, and backup the most critical parts in the cloud as well; all backups are encrypted both at rest and in transit.
- Supply chain/internet provider service interruption. We have put 4 ISPs in place, including a direct link to a Polish ISP which is used as the default link. We have also set up Starlink terminals in our offices in Lviv for additional protection from conventional service interruptions.
- DDoS attacks. Our experts have put in place ISP’s mitigation controls and enabled on-premise NGFW anti-DDoS services.
5. Cutting traffic from Russia and Belarus
Finally, our security team suspended all traffic coming from russia and belarus on our office firewalls as soon as the invasion began, making it impossible for any cyberattacks to come from IPs associated with these countries. This was one of the measures taken by many local institutions from various industries, which played a big role in maintaining a stable state of cybersecurity in Ukraine.
Ukraine’s defense remains strong on all fronts
While the brave people of Ukraine protect their land from the russian invaders, local IT experts maintain a strong line of defense against cybersecurity threats in Ukraine that come from russian-sourced hackers. The surge of malicious activity that Ukraine has experienced in the first days of the invasion has since decreased and new attacks are being mitigated by the combined forces of the Ukrainian authorities and volunteers.
The IT industry itself was among the least affected by the russian war in Ukraine. Most companies were able to quickly relocate their employees to safety and maintain the pre-war levels of delivery. As a result, many global businesses not only continue their cooperation but also expand or form new partnerships with local service providers.
Get a complete overview of the 2025 software development market in Ukraine!


Success!

