Along with a myriad of opportunities, today’s technological revolution brings a number of threats and challenges for digital leaders. Data security continues to be a serious concern for most companies, thus rising the demand for advanced security automation, threat intelligence, and security analytics. According to Gartner, by 2020 the worldwide spending on information security is expected to top $113 billion with an increase of 7.6%.
Realizing the growing security risks in the legally complex and increasingly regulated global economy, software development outsourcing companies put a lot more emphasis on complying with industry regulations, policies, methodologies, and technologies used to protect data. They conclude well-thought-out service-level agreements (SLAs) with their clients and look for more efficient solutions for responding to potential vulnerabilities in the development process and tackling the security challenges.
With more than 15 years of experience on the IT market, we understand the importance of information security when working with international clients. Therefore, we’d like to share our knowledge and experience in the most effective information security procedures when outsourcing software development.

Source: Statista
Information Security Management
Since information is the most valuable business asset, it needs to be well protected. Today no one can name the exact figure of total losses from unauthorized access to information. However, one thing is certain – this figure is huge.
Any modern enterprise, regardless of its field of activity, is unable to successfully operate on the market and progress without the information security management system. By properly identifying potential threats and vulnerabilities as well as carrying out systematic risk assessments, your software development vendor can select the most appropriate controls to manage any risks. In such way you can be sure that your sensitive data is under effective protection of your trusted IT partner.
The British Standards Institution (BSI) and the International Organization for Standardization (ISO) supported by the largest commercial organizations such as Shell, National Westminster Bank, Unilever, and others have developed a globally recognized information security standard ISO/IEC 27001. It defines how to organise information security and enables organizations to assess their risks and implement appropriate controls to preserve confidentiality, integrity, and availability of information assets.
In accordance with the requirements of the ISO standard, an organization must consider and assess the specific risks to which its activities are exposed in terms of preservation, confidentiality, and integrity of information. Such Ukrainian IT outsourcing companies as N-iX, Sigma Software, Eleks, Ciklum, SoftServe, and others have already passed ISO certification to ensure their clients security.
Cooperation with ISO-certified IT vendors allows companies to:
- provide information security guarantees to their customers, investors, and other stakeholders;
- reduce the number of incidents and the costs associated with unauthorized access and potential information loss;
- ensure safe management of information resources;
- raise the company’s profile and facilitate interaction with customers;
- increase the overall efficiency of doing business.
On the whole, any trustworthy IT vendor must have an effectively implemented documentation and records management system, established security policy, and efficient process control. That’s why, when choosing an outsourcing provider, it’s essential to consider only those IT companies which are compliant with ISO standards and requirements. This means that all of their internal processes and departments passed an external audit to ensure they are providing the best quality of services and the highest security levels at all stages of cooperation.
Additionally, it’s important to conclude thorough service-level agreement (SLA) with your offshore provider. The SLA should describe security measures and mechanisms, security awareness of the outsourced team, security response and alerting processes, patch remediation time, and other critical details.
General Data Protection Regulation
ISO is not the only certification an outsourcing provider must have to protect your product from possible risks and vulnerabilities. For instance, the General Data Protection Regulation (GDPR) will have a far-reaching impact on global organizations as it will replace the primary law regulating personal data protection – Data Protection Directive 95/46/ec in Spring 2018.
The new standard urges software development companies to implement appropriate security initiatives and ensure their organizations remain compliant when the new rules go into effect. To comply with GDPR requirements software development providers have to go through the following procedures:
- Gap analysis
The first thing organisations need to do to comply with the GDPR is to perform a gap analysis between how their current processes and systems handle data and what would need to be changed in order to meet the new requirements.
- Early security evaluation
Another core idea behind the new GDPR is building data security and privacy into the application or system from the outset. This means that security and privacy need to be considered at the initial stages of the Software Development Life Cycle (SDLC).
- Risk assessment
As part of the EU GDPR, organisations are required to ensure a level of security appropriate to the potential risk level. This includes encrypting and pseudonymisation of personal data in order to mask the most identifying fields within data records.
In the case of a breach or technical incident, organisations should have the ability to restore the availability of personal data in a timely manner. They are also required to ensure the confidentiality, integrity, and availability of data processing systems and services as well as set up a process for regularly assessing and testing security practices.
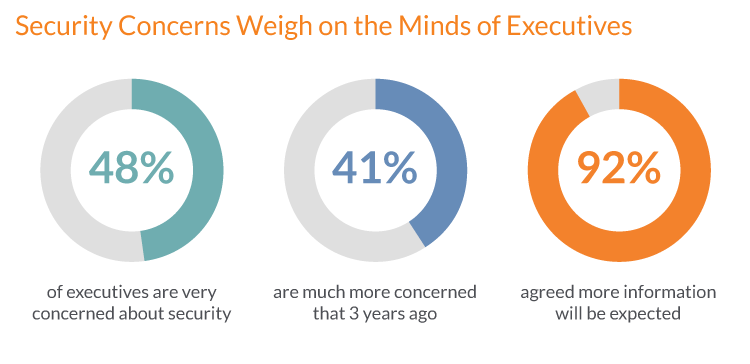
Source: Cisco
How we tackle information security challenges?
N-iX has embedded high standards for data security and formed a separate department to regulate security-related issues. The company has cooperated with international customers from highly-regulated industries such as fintech, healthcare, manufacturing, energy and others. Therefore, we understand the importance of performing regular audits to meet industry standards.
N-iX has a well-defined information security policy and the information security management system. Our dedicated team for information security consists of administrative and technical security professionals that act in accordance with the ISO 27001 standard requirements. We have successfully completed the ISO 27001 certification to make sure our company meets all legal, statutory, regulatory, and contractual requirements. The external audit of the company was performed by Bureau Veritas, a globally recognized leader in the certification industry.
Additionally, N-iX has implemented a security plan for business continuity and disaster recovery. By joint efforts of our infosec experts, our security management system is being regularly tested and updated in accordance with new advancements and potential system vulnerabilities. Moreover, our security specialists conduct regular information security walk-throughs for our team members and perform a background check of every potential candidate and client. Thus we cooperate with reputable subcontractors who comply with our security requirements and sign non-disclosure agreements to ensure customer security. The above-mentioned procedures help us identify and implement actions that will avoid any risks and provide the highest level of information security to our clients.
Afterword
Integrity and privacy must remain the highest priority of every company, especially when outsourcing software development. However, not all IT providers work side by side with compliance and data protection specialists and audit teams to get continuous improvement of their information security systems. That’s why it’s important to make sure your potential IT partners comply with the GDPR and ISO requirements and apply the most efficient information security practices. Only by working together with your IT vendor, can you ensure the protection of your information assets from the modern cyberthreats.



