How do you protect a digital ecosystem that spans multiple cloud providers, platforms, and compliance frameworks? Can you maintain full visibility and control when each environment follows its own rules? The fragmented nature of multi-cloud systems makes it increasingly difficult to maintain sufficient security. According to IBM, in 2024, 40% of breaches involved data stored across multi-cloud and hybrid environments. These incidents cost organizations over $5M each and took 283 days on average to identify and contain—the longest period, compared to an average of 224 days for breaches involving data stored exclusively on-premises. Multi-cloud security has become a defining factor of business resilience and trust.
Building strong cloud security requires a cohesive, forward-looking approach that aligns technology, governance, and expertise. Explore our guide to discover actionable best practices and learn how to address the most pressing challenges in securing complex multi-cloud environments.
Top 10 multi-cloud security best practices
Securing a multi-cloud infrastructure requires more than simply relying on traditional cloud security practices. Given the complexities of managing multiple platforms, organizations must implement robust, multi-layered strategies. Here are 10 essential best practices to protect your business across different cloud providers.
1. Implement a unified security strategy
A unified multi-cloud security strategy is essential for consistent protection across all cloud environments. With different providers offering varying security protocols, organizations risk leaving vulnerabilities unaddressed. A centralized strategy with integrated security policies and tools enables better visibility and faster response times across all platforms. This approach reduces risks, simplifies management, and ensures that all teams adhere to the same standards.
Read more: How to adopt and manage multiple cloud platforms
2. Implement identity and access management (IAM)
Keeping track of who has access to which resources can be challenging in complex cloud environments. This becomes even more critical in multi-cloud security, where different platforms add layers of complexity. A strong IAM framework establishes clear controls, ensuring only the right individuals can access the right assets and significantly reducing the potential attack surface.
Our experts define IAM’s most essential components and practices as follows:
- Role-based access control (RBAC): Assign permissions based on users’ roles and responsibilities to limit unnecessary access.
- User identity federation: Link user identities across multiple platforms to simplify access management.
- Regular audits: Review user access rights regularly to ensure individuals only have access to the data and applications necessary for their current roles.
- Audit trails and logs: Maintain detailed records of user activity to identify suspicious actions.
3. Collaborate with cloud technology consultants
Partnering with experienced cloud consultants can significantly strengthen your multi-cloud security strategy. These experts help you assess risks, align configurations with best practices, and coordinate with cloud providers to ensure consistent protection across environments. By using specialized multi-cloud security services, you can enhance visibility, improve compliance, and proactively address vulnerabilities before they become business threats.
N-iX, for instance, supported Lebara, a major European telecom provider, in adopting a multi-cloud strategy across AWS and Azure. By enabling scalable and cost-efficient infrastructure with automated CI/CD pipelines, the N-iX team demonstrated the value of deep cloud expertise. The same experience and practical cloud engineering skills are essential when implementing effective, enterprise-grade multi-cloud security.
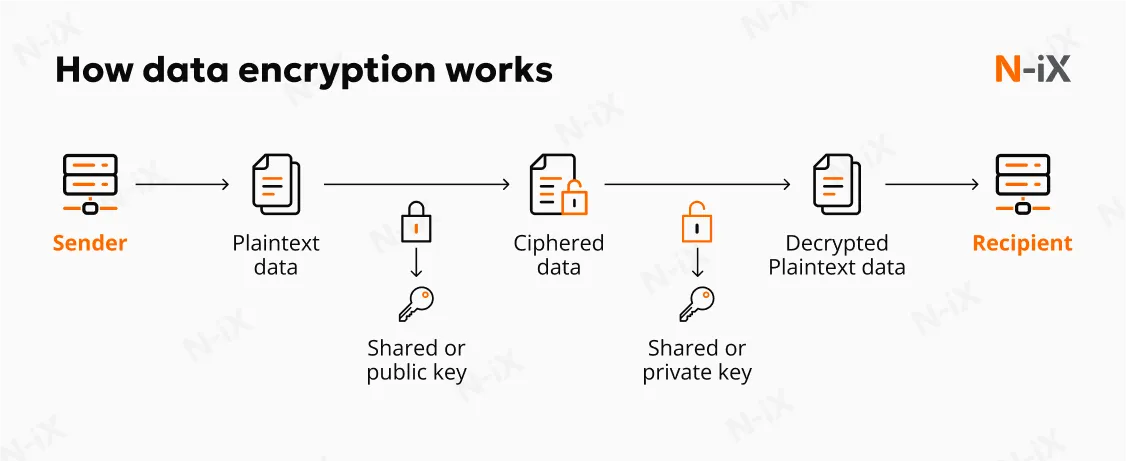
4. Use encryption for data at rest and in transit
Encryption is a cornerstone of multi-cloud data protection, ensuring sensitive information stays secure across different platforms. Since data is frequently stored and transferred between providers, it can be exposed to unauthorized access. Encrypting data both at rest (when stored) and in transit (when moving) safeguards it regardless of where it resides or how it travels.
Most cloud providers offer built-in encryption tools, making it easier to integrate this practice into your security strategy. Additionally, end-to-end encryption ensures that even if data is intercepted, it cannot be read without the decryption key.
5. Implement automated security solutions
Managing the security of your multi-cloud environment manually is like trying to guard multiple doors at once. Eventually, something will slip through. Automated multi-cloud security solutions strengthen resilience by accelerating threat detection, patching, and response, minimizing human error while freeing teams to focus on higher-value priorities.
Key areas where automation can enhance security include:
- Patch management: Keep environments up to date with the latest security updates.
- Threat detection: Identify suspicious activity in real time across platforms.
- Incident response: Predefine actions for common threats so your system can react to attacks without human intervention.
- Compliance monitoring: Continuously check configurations against regulatory requirements.
6. Regularly update and patch systems
Cybercriminals often exploit known vulnerabilities, so delaying updates can leave your cloud environments exposed. Regularly applying patches across all platforms closes security gaps before attackers can take advantage. Establish a clear schedule, monitor vendor advisories, and test critical updates before deployment. Staying disciplined with updates keeps your multi-cloud environment resilient against evolving threats.
7. Conduct security assessments and penetration testing
Even the most advanced defenses can develop weak spots over time. Regular security assessments and penetration testing help you uncover vulnerabilities before attackers do, ensuring your multi-cloud security remains strong. By simulating real-world attacks and reviewing your configurations, you can stay proactive rather than reactive. N-iX experts recommend combining automated scans with manual reviews for the most accurate, actionable insights.
Here are several key assessments and reviews to include in your security strategy:
- Vulnerability scanning: Run vulnerability assessments to continuously identify and remedy weaknesses in your infrastructure.
- Penetration testing: Simulate targeted attacks to uncover hidden vulnerabilities that automated tools might miss.
- Access control reviews: Regularly review IAM policies to ensure permissions reflect current roles and responsibilities.
- Configuration audits: Check cloud configurations for misalignments with your organization’s security policies.
8. Monitor and analyze cloud activity
Real-time visibility is the cornerstone of strong cloud security. Continuous cloud monitoring helps detect anomalies, identify potential breaches, and respond before threats escalate. By consolidating logs and alerts from all providers, you can gain a unified view of your security posture and take swift, informed action when something goes wrong.
To set up effective monitoring:
- Deploy threat detection tools: Use AI-driven security tools to identify attack patterns, such as DDoS attempts, malware, or unauthorized access.
- Centralize monitoring: Aggregate logs and security data from all cloud providers into a single dashboard to simplify analysis and reduce blind spots.
- Establish alerting systems: Set up alerting protocols to notify your team of suspicious activity as soon as it is detected.
- Track user behavior: Analyze login patterns and data access trends to identify compromised accounts or insider threats.
Tip from N-iX experts: Integrate monitoring tools with automated response workflows. This enables immediate containment actions, such as isolating affected instances or revoking credentials, without waiting for manual intervention.
9. Ensure compliance across all clouds
Maintaining compliance in the cloud is one of the biggest challenges organizations face today. Each provider operates under different frameworks and regulations, making it difficult to maintain consistent controls. Aligning policies across all environments is critical to protecting sensitive data and avoiding costly regulatory penalties.
To stay ahead, organizations should automate compliance wherever feasible. Cloud-native tools can continuously assess configurations, monitor data flows, and flag potential violations before they become serious issues. Automated reporting also simplifies audits, saving time and reducing human error.
Beyond automation, maintaining compliance requires strong governance and clear accountability. Define who is responsible for monitoring compliance within each environment and ensure audit logs are centralized and easily accessible. This transparency not only satisfies regulators but also builds trust with clients and partners who rely on your commitment to data protection.
Choose the right EU sovereign cloud provider—get the report!


Success!

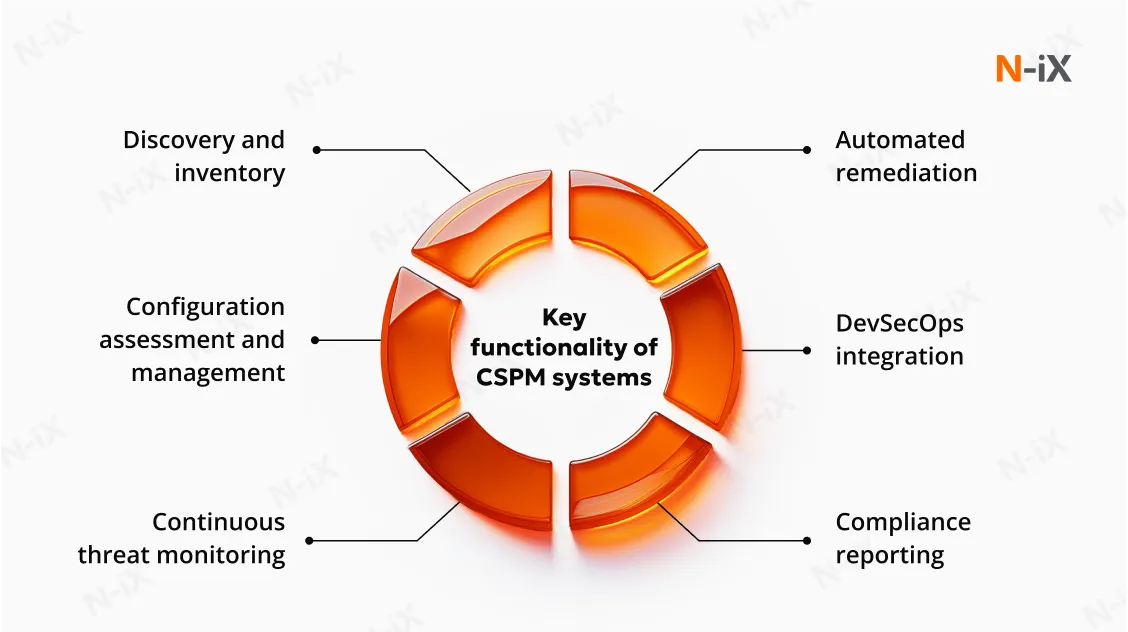
10. Utilize cloud security posture management (CSPM) tools
CSPM tools are essential for strengthening multi-cloud network security. They continuously scan your environments to detect misconfigurations, monitor compliance, and highlight potential vulnerabilities before they become threats. By integrating a CSPM solution, you gain real-time visibility into your entire cloud landscape, allowing you to proactively fix security gaps and maintain a consistent, compliant posture across all cloud platforms.
A well-structured approach and the right technologies can significantly enhance your security posture. However, real-world implementation often brings unique challenges that require careful navigation. Let’s explore what these challenges are and how you can tackle them effectively.
How best practices address key multi-cloud security challenges
Managing security across multiple cloud platforms introduces complexity that cannot be addressed with uncoordinated tools or reactive measures. The following challenges show why the security best practices we defined are essential in a multi-cloud setup.
1. Unified security strategy prevents fragmented visibility
When each cloud provider uses different tools, settings, and policies, gaining a clear view of your security posture becomes difficult. This fragmentation increases the risk of blind spots where threats can go undetected.
A unified multi-cloud security strategy addresses this challenge by centralizing monitoring, access control, and policy enforcement. Practices such as continuous cloud activity monitoring, IAM standardization, and CSPM integration help security teams see the entire environment at once and react to threats faster.
2. Strong IAM reduces the attack surface and access misuse
Managing access across multiple platforms increases the risk of privilege misuse, orphaned accounts, or excessive permissions. These are common entry points for breaches.
Strong IAM practices address this challenge by enforcing least privilege, enabling identity federation, and applying role-based access controls consistently across providers. Regular audits and access reviews reduce unnecessary privileges and help detect compromised accounts before they lead to major incidents. This also limits lateral movement in case of credential compromise and significantly reduces the attack surface.
3. Automated security tools prevent misconfigurations and drift
Misconfigured storage, exposed endpoints, and inconsistent security rules across clouds are major vulnerabilities. Configuration drift often happens gradually as teams make changes in separate cloud accounts without centralized control.
Automated security and compliance checks directly address this challenge. CSPM tools and continuous configuration audits identify risky settings across all cloud accounts, while automated patching and remediation reduce exposure without requiring constant manual oversight.
4. Continuous compliance reduces regulatory risk
Different regions and industries impose strict compliance requirements such as GDPR, PCI DSS, and ISO/IEC 27001. Meeting these standards across AWS, Azure, and Google Cloud at once can be overwhelming without proper governance.
Automated compliance monitoring and policy enforcement simplify this complexity. By integrating compliance checks into CI/CD pipelines and maintaining audit logs, organizations can ensure ongoing alignment with regulatory requirements and avoid costly violations.
Why partner with N-iX to strengthen your multi-cloud security?
- We bring 23 years of experience in technology consulting, helping enterprises across finance, energy, healthcare, retail, and over 20 more industries build secure and scalable cloud systems.
- Our team comprises over 2,400 professionals, including more than 420 cloud engineers and dedicated security experts.
- As an AWS Premier Tier Partner, Microsoft Solutions Partner, and Google Cloud Platform Partner, we understand provider-specific security nuances and how to bridge them.
- We comply with major industry standards, including ISO 27001, SOC 2, PCI DSS, and GDPR, ensuring your security posture is robust and audit-ready.
- In the last five years, we’ve completed over 250 cloud and security projects, equipping our team with practical expertise in managing and securing multi-cloud ecosystems.
- We offer end-to-end support: from security assessments and architecture design to implementation, monitoring, and continuous improvement across environments.
Have a question?
Speak to an expert