If your security team monitored every camera feed in real time, your incident rate would look very different, very different because most issues would be detected at the moment they occur, rather than hours later during manual review. But no enterprise operates that way; the workload scales faster than people can keep up. Operators juggle dozens of screens, alerts blend into background noise, and critical events often appear prominent only after a post-incident review. This is why more organizations are turning to computer vision development services to consistently interpret video data, detect risks earlier, and support security teams with reliable, real-time insights.
Computer vision in security aims to make large, complex environments observable in ways that traditional surveillance can't. It notices when a restricted zone is breached, when safety procedures aren't followed, or when movement looks inconsistent with normal operations. And it does this without relying on constant manual oversight.
When an unauthorized person slips through an access point or when a worker enters a restricted zone without protective equipment, timing determines the outcome. Noticing it within seconds allows teams to respond before the situation escalates. Noticing it an hour later leads to measurable impact: safety incidents, financial losses, regulatory exposure, and in many cases, operational downtime. In this article, you'll learn:
- How does computer vision improve security outcomes
- Which security use cases benefit most from computer vision today
- What privacy, governance, and regulatory requirements shape CV deployments
- What challenges typically undermine computer vision accuracy and reliability
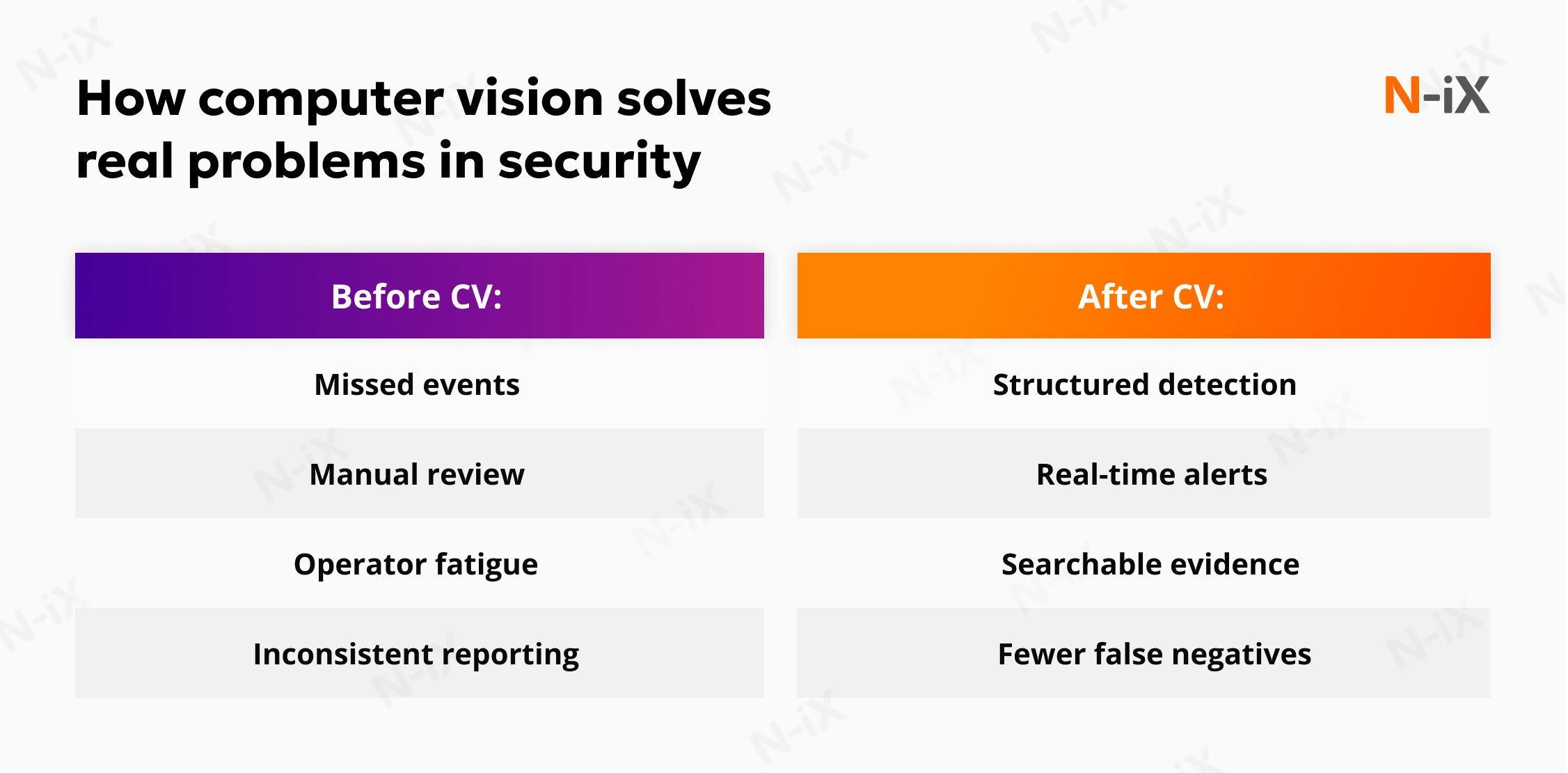
How computer vision solves real problems in security
In most organizations, security incidents rarely appear as singular, dramatic events. They build up from minor, often unnoticed deviations. For instance, it could be an entry point misused, a moment of unsafe behavior, a vehicle taking an unusual path, or an asset handled outside standard procedure. These moments look unremarkable in isolation, and traditional monitoring systems often fail to interpret them. Computer vision changes this dynamic by evaluating visual information continuously and translating it into structured signals that security teams can rely on.
In operational environments: Complexity that humans cannot consistently absorb
Large facilities generate a steady flow of visual activity across factories, warehouses, ports, campuses, retail locations, or transportation hubs. A traditional camera network simply records these events; it does not understand or contextualize them. Computer vision systems detect motion patterns, object interactions, access behaviors, deviations from everyday routines, and environmental risks in real time.
Security performance collapses when vigilance depends on individual attention. Computer vision brings consistency: every frame evaluated, every anomaly measured, every alert backed by data.
For physical security teams: Consistency in environments where timing matters
Security teams need systems that behave predictably even under pressure. Computer vision provides the same level of vigilance regardless of workload, environmental conditions, shift changes, or human fatigue. It identifies perimeter breaches, tailgating at access points, loitering near sensitive areas, abnormal movement patterns, and unauthorized handling of equipment.
For safety and compliance programs: Visibility into behaviors that influence incident rates
Workplace safety often depends on adherence to well-defined procedures. Whether it's wearing protective equipment, maintaining safe distances from machinery, following vehicle routes, or respecting restricted zones, small deviations create measurable risk. Computer vision in security systems enables organizations to monitor compliance passively, without disrupting operations or relying solely on manual checks.
For access control and investigations: Evidence that is searchable and audit-ready
Incident investigations often require hours of manual video review, especially when multiple cameras must be correlated. Computer vision reduces the time needed for forensic analysis by indexing visual events as they happen: who entered, where, when, how long they stayed, and what interactions occurred.
For environments with mixed traffic: Understanding movement and detecting anomalies
Facilities that combine pedestrian, vehicle, and equipment traffic present unique challenges. Near misses, unsafe crossings, unauthorized vehicle movement, and unexpected load handling are common risk points. Computer vision parses these complex scenes by tracking trajectories, identifying interactions, and assessing whether behaviors align with expected patterns.
For multi-site operations: Standardization across locations with different conditions
Enterprises often struggle with inconsistent security performance across sites. Local practices vary, camera quality differs, and incident reporting is uneven. Computer vision enables standardized detection rules and expected behaviors across multiple facilities, ensuring every site benefits from the same level of scrutiny and incident awareness. The system adapts to each environment (indoors, outdoors, variable lighting, crowds, open spaces), but applies a unified logic to interpreting events.
What are the use cases of computer vision in security?
1. Biometric authentication and access control
Identity verification sits at the foundation of facility security, yet most access control systems rely on mechanisms that can be borrowed, shared, duplicated, or misused. Computer vision enhances access control by validating identity using physical and behavioral features rather than artifacts such as cards or codes.
Modern facial recognition systems analyze a wide range of facial landmarks and textures using deep learning architectures trained on large, controlled datasets. When integrated with access control systems, they confirm whether the person approaching a door is the one associated with a credential, removing ambiguity in cases where badges are lost, stolen, or shared. In high-traffic facilities, this reduces unauthorized entry and improves flow efficiency without imposing friction on personnel.
Face-based authentication must also address deliberate attempts to deceive the system. Computer vision in security systems provides liveness detection and anti-spoofing safeguards to distinguish real faces from printed photos, screen replays, deepfake videos, and masks. These models analyze micro-movements, reflectance patterns, and temporal changes to ensure the identity presented is authentic.

Computer vision in security supports iris recognition by segmenting and encoding the unique textures of the iris, providing accuracy suitable for data centers, laboratories, or government facilities where access must meet stringent thresholds. Vision-driven fingerprint recognition enhances traditional biometric systems by improving feature extraction even in suboptimal lighting or environmental conditions. Beyond direct authentication, computer vision monitors entry behaviors, identifying attempts to enter behind another person, group entry under a single authorization, or irregular movement patterns near access points.
While iris recognition offers strong accuracy under controlled conditions, real-world performance often drops due to glare, motion, variable lighting, and reflections from glasses or contact lenses. Modern CV pipelines compensate for these factors with multi-frame analysis and quality scoring, but reliability still depends heavily on environment and sensor placement.
2. Video surveillance and physical security
Modern surveillance networks capture extensive footage, but human operators rarely see more than a fraction of it in real time. Computer vision in security and surveillance continuously processes these streams, identifying security-relevant events and elevating them immediately.
Threat and anomaly detection
One of the central questions in security today is straightforward: how many early warning signs does your organization miss simply because no one sees them in time? Computer vision addresses this by monitoring every camera feed continuously and scoring behavior against learned patterns of normal activity. CV analyzes posture, trajectory, motion intensity, and interpersonal interactions in real time. This allows the system to surface events that would typically blend into the background (prolonged loitering near controlled doors, sudden bursts of running in restricted areas, evasive body language, attempts to obscure one's face, or clustering of people in low-traffic zones).
Another question that security teams often struggle with is: what else goes unnoticed when activity occurs at perimeters, remote facilities, or infrastructure sites where humans are rarely present? Here, computer vision extends visibility by defining virtual boundaries within video scenes and triggering alerts when someone enters high-risk zones such as loading bays, server rooms, substations, or fenced industrial areas.
Typical outputs from threat- and anomaly-detection systems include:
- Alerts on behavior that deviates from established patterns
- Unauthorized access or perimeter breaches detected through virtual zones
- Real-time identification of weapons or prohibited objects
- Detection of abandoned or suspicious items in public areas
- Indicators of tampering, smoke, or structural anomalies at critical sites
- Behavioral signatures associated with ATM and kiosk fraud
Object tracking and identification
Most incidents do not happen within the field of view of a single device. They unfold across hallways, parking lots, loading docks, stairwells, or large outdoor areas. Computer vision in security addresses this by maintaining persistent awareness: tracking individuals, vehicles, or objects across cameras while preserving identity continuity.
Person detection is the foundational capability that everything else builds on. Systems must reliably determine who is present in each frame before they can track movement or identify anomalies. Modern models detect people under diverse conditions and anchor those detections in time and space. When needed and in compliance with legal and ethical frameworks, this detection layer can be paired with identity recognition, enabling organizations to locate persons of interest, enforce exclusion lists, or support missing-person searches across large campuses or transportation hubs. In these scenarios, accuracy and governance matter as much as the technical models themselves.
Vehicle monitoring expands this situational awareness. Automatic Number Plate Recognition (ANPR) systems capture and interpret license plates as vehicles enter and exit facilities, integrating this data with access control systems, delivery logs, and incident management workflows. Drone-augmented surveillance addresses this by extending monitoring to remote or expansive areas, such as forests along perimeters, border regions, industrial yards, rooftops, or utility corridors. These drones can be dispatched for routine patrols or launched in response to a triggered alert, enabling operators to assess situations that cannot be evaluated from ground-level cameras alone.
Master real-time precision with edge computer vision—get the practical guide!


Success!

Across the application of computer vision in security, object tracking, and identification systems support:
- Continuous visibility of people and vehicles across multiple cameras
- Reconstruction of movement paths during investigations
- Detection of irregular, unauthorized, or suspicious mobility patterns
- Automated logging of vehicle entries and exits through ANPR
- Extension of surveillance coverage through drone-enabled CV
For example, in one deployment, N-iX helped a global transport-solutions provider develop real-time models for seat-belt enforcement and distracted-driving detection, achieving accuracy exceeding 90%. These outcomes underscore why assessing real-world conditions and tuning models to your specific environment matter as much in security as they do in traffic surveillance.
Public safety
Computer vision expands situational awareness by continuously assessing how people move, gather, and interact with their surroundings. It evaluates crowd density, flow direction, and unusual behavior in areas where movement is usually steady.
Public safety depends on the ability to recognize early signals that something is shifting from routine to risky. Computer vision strengthens this visibility by continuously analyzing how people and vehicles move through an environment. Crowd density, direction of flow, abnormal gathering, sudden surges toward exits, or erratic individual behavior are surfaced as real-time alerts rather than being discovered after the fact. The same visual intelligence applies to emergencies: smoke, fire, spills, electrical anomalies, and personal distress events such as falls or loss of consciousness are detected quickly, often before traditional sensors respond.
Safety oversight extends to vehicle and infrastructure management. Computer vision in security systems monitors internal traffic patterns, detects stalled vehicles, identifies collision risks, and tracks driving behavior in logistics yards, industrial sites, and busy campuses. PPE compliance is enforced automatically by verifying whether workers are wearing the required protective equipment in mandated zones, reducing reliance on manual checks and improving accuracy. Inside vehicles, driver-monitoring models evaluate gaze, head position, and posture to detect distraction or fatigue.
Across these settings, computer vision provides:
- Early recognition of crowd-related risks
- Rapid detection of environmental or personal emergencies
- Continuous vehicle flow and hazard monitoring
- Automated PPE and safety-behavior compliance
- Identification of driver fatigue and distraction
3. Cybersecurity and information security
As digital and physical infrastructures converge, the attack surface grows in ways traditional monitoring tools rarely anticipate. Computer vision in cybersecurity adds a layer of defense by analyzing the visual elements of digital interactions. Phishing and spoofing attempts frequently rely on visual deception, such as altered brand logos, manipulated QR codes, or near-identical interface components. CV-based filters examine these visual cues directly, identifying inconsistencies that bypass text-based scanners and flagging assets designed to mislead users or evade traditional fingerprinting.
Beyond social engineering, computer vision contributes to malware detection using binary visualization. Here, file contents are transformed into image-like structures that reveal patterns characteristic of malicious behavior. These models catch variants that signature-based systems miss, improving detection of zero-day or polymorphic threats. Traffic anomaly detection extends protection further: CV-based models analyze network flow visualizations to surface deviations in intensity, structure, or timing that often precede an intrusion.
Another emerging challenge, deepfakes, is addressed through the same principles. By examining pixel-level artifacts, lighting irregularities, and motion inconsistencies, computer vision in security systems can identify AI-generated media used to impersonate individuals, manipulate surveillance footage, or support fraud. Even the security systems themselves benefit: computer vision monitors camera access, detects unauthorized attempts to manipulate streams, and ensures the integrity of video sources by verifying consistency between expected and actual outputs.
4. Forensic and investigative support
Computer vision also reshapes how organizations conduct investigations and compliance reviews. Instead of manually reviewing hours of footage, analysts can run queries that describe what they are looking for: "a blue sedan entering after 10 p.m.," "an individual with a backpack near the north entrance," or "all instances of a fall in Zone C." This makes video archives searchable and dramatically cuts the time needed to reconstruct events or validate claims.
Real-time tagging and indexing ensure that evidence is not only collected but properly structured. Each clip can be linked to location, timestamp, detected objects, recognized individuals (where legally permitted), and contextual anomalies. This level of organization supports internal investigations, insurance processes, regulatory reporting, and law enforcement collaboration.
What are the privacy, governance, and legal considerations of computer vision in security?
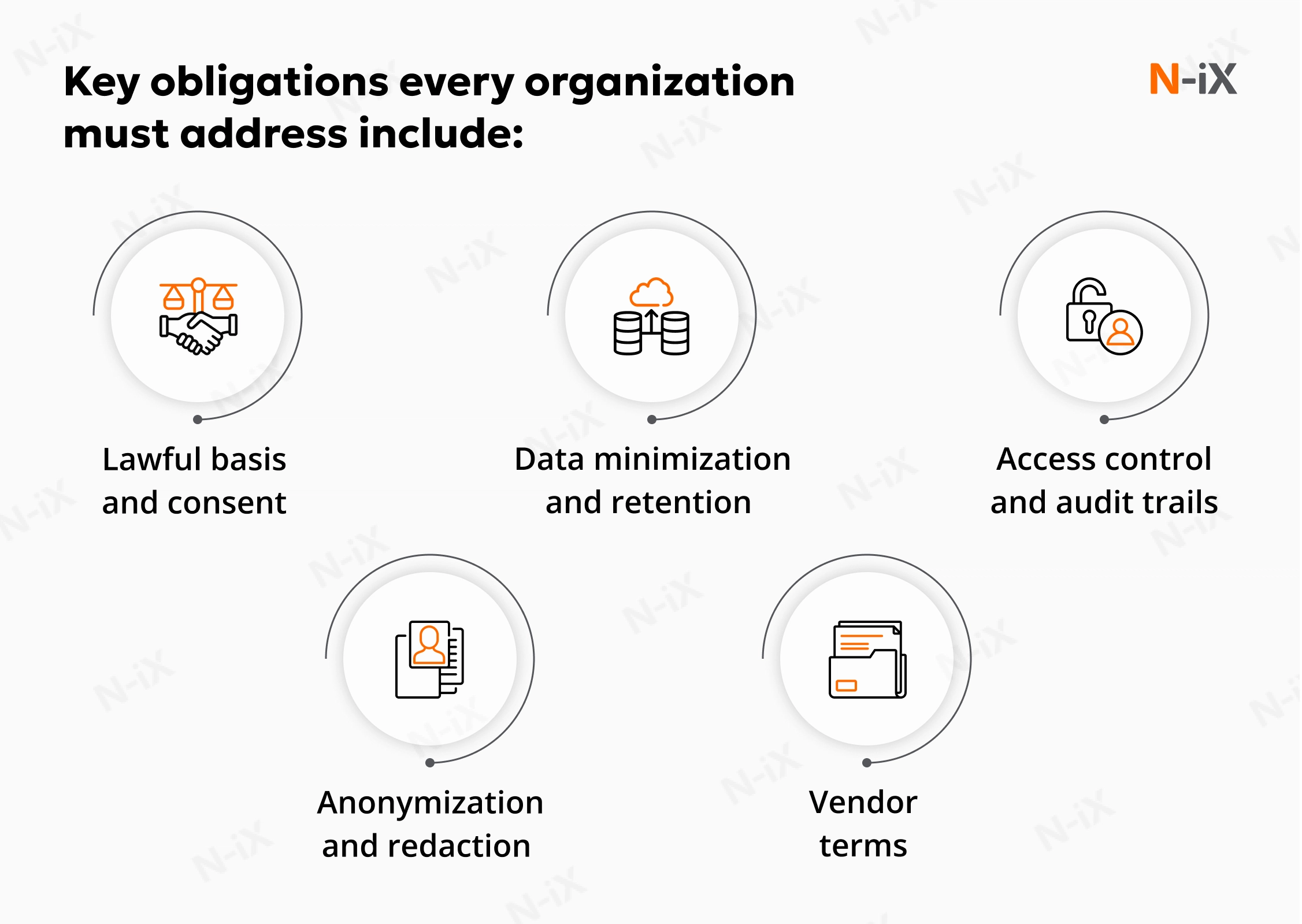
The strategic value of computer vision in security cannot be separated from its regulatory and ethical obligations. These systems process visual information that increasingly includes biometric identifiers, elevating deployment from a technical decision to a high-stakes governance and compliance responsibility. Regulations such as GDPR and the upcoming EU AI Act treat biometric data and persistent monitoring as high-risk categories, requiring explicit justification, strict purpose limitation, and clear retention policies.
Any organization implementing CV must be prepared to document why the technology is necessary, how data is collected, how long it is stored, and who has access to it. Without these safeguards, the legal exposure is substantial: unlawful biometric processing can result in multimillion-dollar penalties, litigation risk, and long-term reputational damage.
The governance challenge extends beyond regulatory checklists. CV systems generate continuous observational data, which can lead to internal misuse, biased enforcement, or mission creep. To prevent these outcomes, organizations must define a governance model that establishes who can view, extract, annotate, export, or escalate video-based evidence. Role-based access control, immutable audit logs, and human-in-the-loop decision checkpoints are essential for accountability, especially in environments that use face recognition, employee monitoring, or automated incident scoring.
When implemented responsibly, CV can meet both security objectives and compliance obligations. The technical safeguards, encrypted video streams, local inference pipelines, anti-spoofing controls, and network hardening must be paired with clear, documented, and continuously reviewed procedural oversight. Effective governance does not slow down security operations; it protects them from regulatory risk, public scrutiny, and internal disputes about data ownership or algorithmic fairness.
What challenges can undermine computer vision security systems?
Computer vision delivers measurable benefits to modern security operations, but only when the underlying assumptions, data governance, and infrastructure are carefully designed. Most unsuccessful deployments fail for predictable, avoidable reasons. Over the past decade, N-iX has delivered CV solutions across manufacturing, transportation, retail, telecom, and public safety, and the same patterns appear everywhere: AI performs well only when engineering discipline, domain-specific modeling, and strong governance frameworks are applied from the start.
This section outlines the challenges that cause CV systems to underperform and explains how N-iX's approach systematically prevents them.
Technical and environmental limitations
Technical reliability is the most common source of degraded performance. AI models depend entirely on the quality of the visual input they receive. When cameras are placed poorly, operate in inconsistent lighting, capture low-resolution footage, or experience blind spots or occlusions, detection accuracy declines sharply. Older hardware introduces noise, inconsistent frame rates, and motion blur that even advanced models cannot fully compensate for.
False positives are another predictable outcome. When systems generate too many questionable alerts, human operators begin to ignore them, creating "alarm fatigue" and eroding trust in the technology. N-iX addresses this early by conducting structured environment and camera audits, including field-of-view analysis, lighting variability assessments, occlusion mapping, and video-quality baselining. Our teams pilot models across multiple conditions (day/night cycles, weather changes, seasonal lighting shifts) so that accuracy under the same constraints the system will face in production. This prevents the most common cause of CV failure: discovering infrastructure limitations only after the system is already deployed.
Accountability gaps
The next set of challenges stems from governance. CV technologies routinely process biometric and behavioral data, which brings them under the scope of GDPR, CPRA, BIPA, workplace-monitoring laws, and the upcoming EU AI Act. Deployments without documented purpose limitation, data minimization, or controlled retention windows expose organizations to fines and reputational risk.
Operationally, the absence of role-based access control, immutable audit logs, and clear oversight responsibilities creates internal vulnerabilities. Without a governance framework, who is authorized to view sensitive footage? Who reviews automated decisions? How are contested alerts handled? These issues determine whether a system supports accountability or becomes a liability that is difficult to audit or defend.
N-iX embeds governance into the computer vision in security systems. The process includes purpose limitation, data minimization, edge anonymization, configuration of retention policies, role-based access control (RBAC), immutable audit logs, and human-in-the-loop validation for high-impact decisions. We also support DPIA preparation, documentation for legal reviews, and the implementation of privacy-by-design practices that align with both EU and US regulatory expectations.
Operational and deployment challenges
CV deployments often fail when organizations assume the technology can slot into existing workflows without redesigning processes around it. Automated detection only delivers value when paired with clear response rules, escalation paths, exception handling, and human-in-the-loop validation for high-impact decisions. Without these structures, CV systems either overwhelm teams with notifications or leave critical events unreviewed.
Infrastructure compatibility is another recurring obstacle. Legacy cameras, outdated NVR/DVR systems, or heterogeneous multi-vendor environments can create inconsistent performance across sites. And because CV models operate in dynamic environments, ongoing maintenance is essential to prevent accuracy decay.
N-iX works with operational stakeholders to map how alerts should be triaged, who has decision rights, when automation is appropriate, and when manual review is required. For organizations evaluating computer vision outsourcing to accelerate deployment or reduce integration risk, we help define SOPs for incident handling, exception management, and performance monitoring. CV becomes a functional part of the security operation rather than an isolated technology layer.
In one of the projects, N-IX improved accuracy by calibrating models on real operational footage, auditing camera placement, and building continuous evaluation into the pipeline; the exact discipline required for reliable threat detection, access monitoring, and anomaly identification. The lessons translate directly: computer vision only works when it is tuned to the environment, validated against real data, and supported by a mature MLOps and governance approach.
Why organizations turn to N-iX for secure computer vision implementation
These challenges are avoidable with the proper planning and expertise. After more than 23 years of delivering data, AI, and computer vision solutions for global enterprises, our teams have developed the engineering discipline, governance frameworks, and cross-functional delivery approach needed to make CV security systems reliable, compliant, and operationally effective. We provide end-to-end computer vision consulting services, from feasibility assessments to model design, tuning, and lifecycle management.
What matters in security is how models behave across your cameras, lighting conditions, and operational patterns. When N-iX designs a CV security solution, we:
- Start with a site and camera estate assessment to understand resolution, angles, blind spots, retention policies, and bandwidth constraints before committing to model performance promises.
- Use real footage from your environment (appropriately anonymized) for data curation and model tuning.
- Build in continuous evaluation from day one: false positives, false negatives, and "ignored alerts" are monitored as first-class KPIs, not an afterthought.
- Plan for model lifecycle management, retraining, A/B testing, and rollbacks to ensure accuracy does not quietly degrade after the initial rollout.
In a recent deployment, N-iX helped a global engineering-technology client overhaul logistics across 400+ warehouses, redeveloping object detection, OCR, and vision pipelines tailored to their environment. The same discipline, site-specific data, infrastructure audit, scalable ML/CV pipelines, apply directly when we build security-focused computer vision systems. If you're ready to explore how to integrate computer vision into security or scale the foundation you already have, let's outline a plan built on clear milestones, verifiable performance, and engineering practices suited for long-term use.
FAQ
Do we need to replace our existing cameras to use computer vision?
In many cases, no. Most CV analytics can run on modern IP cameras as long as they provide adequate resolution, stable positioning, and consistent lighting. During early assessment, N-iX evaluates your current camera estate, identifies blind spots or underperforming units, and recommends minimal upgrades. Many deployments achieve high accuracy by improving placement or lighting.
How accurate is computer vision for security, and what factors affect its performance?
Accuracy varies by use case, environment, and model calibration. With high-quality input and continuous monitoring, CV performs reliably for intrusion detection, object recognition, vehicle analytics, PPE compliance, and anomaly detection. Accuracy drops in low-light, glare-heavy, or occluded scenes, which is why N-iX tunes models using real footage from your environment and tracks performance KPIs such as false positives, false negatives, and drift over time.
How do we prevent false alarms and "alert fatigue"?
False alarms are usually the result of environmental conditions rather than weak algorithms. Reducing them requires a structured approach: assessing camera placement and lighting, tuning models on real operational footage, defining detection thresholds for each zone, and continuously monitoring accuracy. With this discipline in place, alert volume becomes manageable and meaningful, allowing SOC teams to focus on incidents that require judgment, not noise.
Is AI-based video surveillance legal under GDPR, CPRA, or my local privacy laws?
Yes, if implemented within the boundaries of each regulation. Facial recognition, biometrics, and behavioral monitoring are heavily restricted and require explicit purpose definition, DPIAs, retention limits, transparent data flows, and appropriate legal bases. N-iX helps organizations design CV systems that comply with GDPR, biometric privacy laws, and industry-specific requirements by incorporating privacy-by-design, edge anonymization, encryption, and strict access controls.
What infrastructure do we need for AI-powered security?
Requirements for security measures in AI-driven computer vision depend on whether inference runs on the edge, on-premise, or in the cloud. A secure, scalable setup typically includes: reliable IP cameras, edge compute or on-prem servers for real-time inference, encrypted storage aligned with retention policies, and integration with the existing VMS/SOC stack.
References
- Computer-vision research powers surveillance technology - Nature
- Application of computer vision methods for information security - R&E-SOURCE
- A review of computer vision methods in network security - Jiawei Zhao, Rahat Masood, Suranga Seneviratne
- Deep Learning for face anti-spoofing: A survey / surveillance face anti-spoofing - IEEE transactions on pattern analysis
- Emerging tech: Tech innovators in computer vision applications - Gartner
Have a question?
Speak to an expert





