Building a cloud environment that is both globally scalable and compliant presents a growing challenge. Most organizations rely on major public cloud providers, which, despite powerful services, operate under complex jurisdictional rules. Gartner reports that US-based hyperscalers (AWS, Microsoft, Google, IBM, and Oracle) dominate 84% of the cloud market [1]. This geographical concentration raises serious concerns about sensitive data being exposed to foreign jurisdictions.
So, is a rollback to on-premises infrastructures becoming inevitable? No. Enter the sovereign cloud: a new concept that offers compliance without surrendering too much functionality.
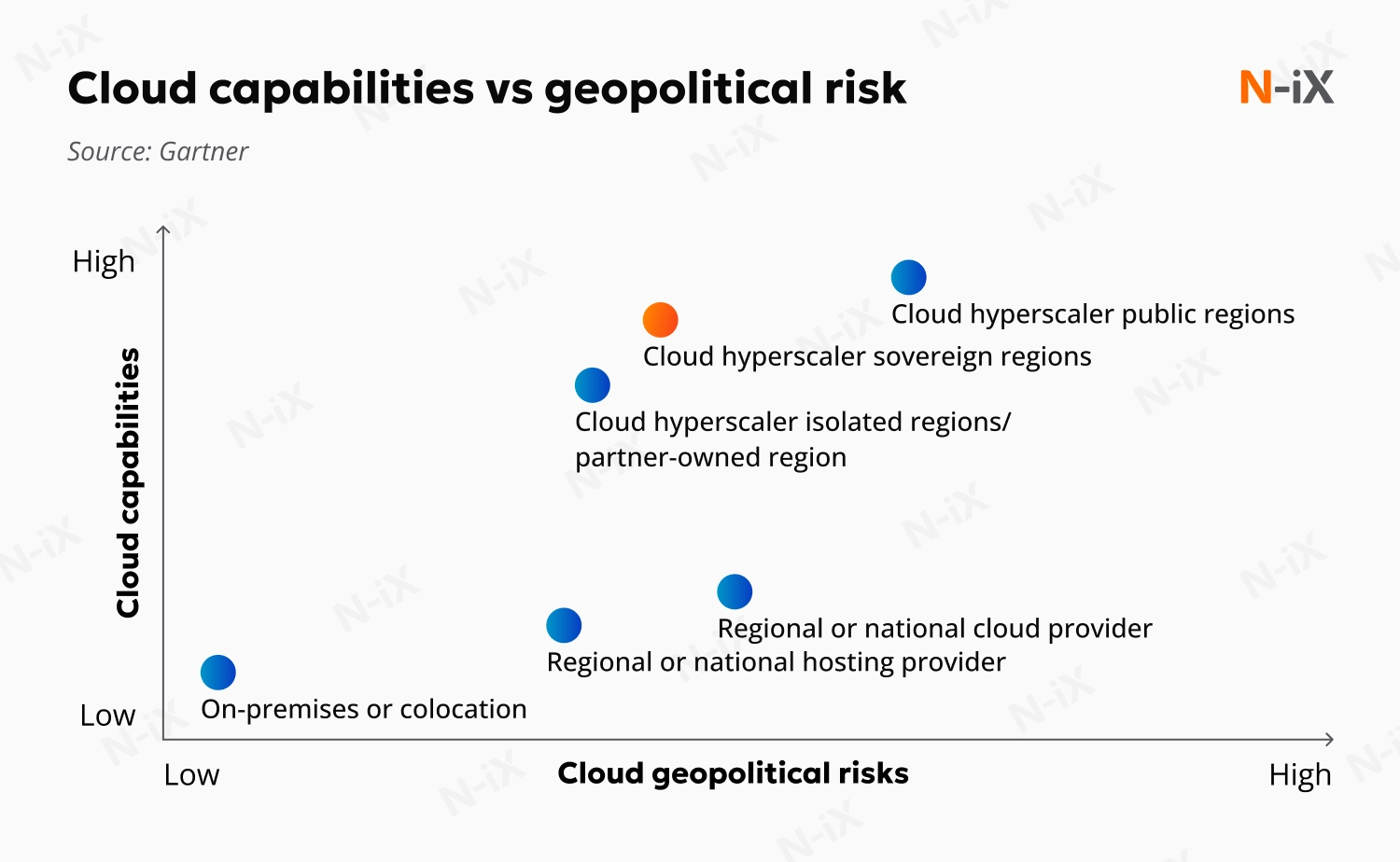
By definition, a sovereign cloud is a cloud computing environment that helps organizations meet its digital sovereignty requirements. But what exactly does that mean, and how is it different from regular public clouds? Follow N-iX experts as they dive into cloud compliance, data privacy, and tips for achieving sovereignty.
What is a sovereign cloud, and why is it important?
Regular cloud architectures are designed for global scalability instead of tight jurisdictional control. They distribute workloads and data storage across regions, focusing on maximizing efficiency rather than staying within particular national borders. This can create serious legal challenges, especially in highly regulated sectors.
N-iX solutions architect specifies that additional issues can arise when laws of different countries clash.
American hyperscalers, such as Microsoft, Google, and Amazon, among others, are subject to the CLOUD Act. This law allows the US government to request access to data stored by these companies anywhere in the world. Those same companies must comply with the GDPR in the EU, which restricts the transfer of personal data to third countries unless certain legal conditions are met. The conflict between these two pieces of legislation (and many others worldwide) is the main driver behind sovereign cloud developments.
Unlike traditional public cloud platforms, a cloud for sovereignty focuses on data access control, legal oversight, and digital independence. It is hosted and managed within the specific country it serves. As a result, such platforms help organizations comply with local data protection laws and reduce the risk of foreign access. This is particularly important for entities handling highly sensitive information, such as government agencies, defense contractors, and healthcare providers.
In sovereign environments, customers get a transparent view of:
- The physical location of the data and computational resources involved;
- The nationality and employment status of staff members who manage the environment;
- The national and international laws governing the cloud environment.
True sovereignty is characterized by a combination of features. It goes beyond controlling where data resides and involves specific infrastructure management, regulatory alignment, and operational oversight.
4 pillars of sovereign cloud architecture
N-iX cloud experts identify the following four prerequisites for creating a secure and compliant sovereign environment:
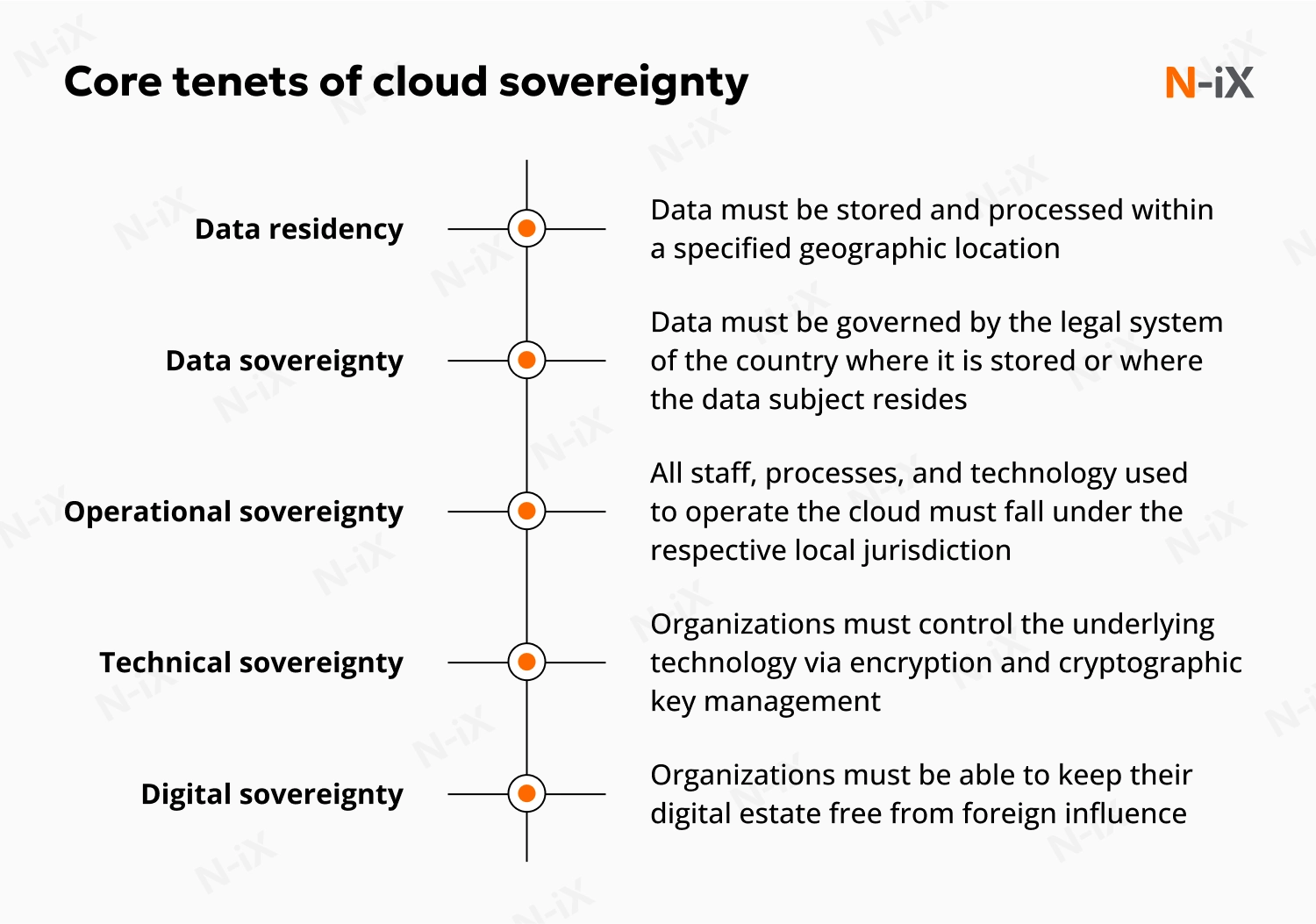
1. Data residency and sovereignty
Data residency refers to the physical location where an organization’s data is stored and processed. It answers a simple question: “In which country are the servers located?” While data residency is a necessary prerequisite for sovereignty, it’s not enough to ensure complete legal protection. Even if your data resides on servers in Germany, for example, it may still be subject to foreign jurisdiction depending on who operates or manages the infrastructure.
Data sovereignty is a comprehensive principle that builds on this foundation. It stipulates that data is governed by the legal system of the country where it is physically stored (or, in some cases, where the data subject resides). It addresses questions of lawful access, jurisdiction, and regulatory control. The goal is to protect against the reach of extraterritorial laws, such as the US CLOUD Act, by ensuring only local authorities can access or demand that data.
2. Operational sovereignty
Operational sovereignty goes beyond data and focuses on who manages your cloud infrastructure. It requires all personnel, processes, and technologies used to operate the cloud to fall under the respective local jurisdiction. In other words, this measure prevents foreign administrators from being compelled to access or alter your systems. Without this control, data residency and legal safeguards cannot provide sufficient protection.
Operational sovereignty addresses the risks of global support models, such as “follow-the-sun.” In these models, staff in different countries can control the organization’s cloud infrastructure at various times during the day and may be asked to access sensitive systems. It answers the vital question: “Who has administrative access to my infrastructure, and what laws are they subject to?”
3. Technical sovereignty
Besides ensuring data sovereignty, organizations must control the underlying technology via encryption and cryptographic key management. This technical guardrail prevents anyone, including the cloud provider, from accessing the data without the customer’s permission.
4. Digital sovereignty
Digital sovereignty is the ultimate strategic objective. It represents an organization’s and, by extension, a nation’s ability to keep its digital estate free from foreign influence. It is a state of digital self-sufficiency that provides resilience against geopolitical shocks and fosters a domestic innovation ecosystem.
Selecting your cloud sovereignty model: 3 strategic approaches
There are three models for achieving sovereignty in the cloud, each with its own advantages and considerations. Let’s explore them in greater detail.
1. The local provider model
In this configuration, a cloud is built and operated by a domestically-owned cloud vendor in your target region. These providers are inherently aligned with their home country’s legal and regulatory requirements.
Key features and how it achieves sovereignty
- Infrastructure: The data centers are located within the country’s borders. They are owned and managed by a local company.
- Personnel: All staff, from administrators to support personnel, are local citizens, ensuring operational sovereignty.
- Legal framework: As a domestic company, the provider is subject only to their country’s laws, offering a clear legal standing against foreign jurisdictions.
- Technology stack: These providers may use their proprietary technology or build their services on open-source platforms, providing a high degree of technical control.
Best suited for: Organizations that require the highest level of protection against foreign influence and want to support a local technology ecosystem. This model is often favored by government agencies and critical infrastructure providers.
Local clouds are exceptionally effective from a regulatory standpoint. However, our experts warn that limited functionality can offset this advantage.
There are smaller cloud providers such as Hetzner and OVHCloud, which are European, but they do not yet offer the same level and diversity of capabilities as hyperscalers. You may also miss out on global scalability, a broader service ecosystem, and emerging innovations (such as AI services).
To avoid shrinking your options where it’s not absolutely necessary, engage with a reliable cloud consulting and development firm like N-iX. An experienced consultant can help determine which workloads require a dedicated local environment and identify those that can stay on larger feature-rich clouds.
Read more: Your guide to cloud consulting in Europe
2. The hyperscaler partnership model
This model involves a global cloud provider (like AWS, Microsoft, or Google) partnering with a local entity or creating a legally distinct subsidiary in the target country. On the one hand, it offers a balance between sovereignty and access to extensive cloud services. Conversely, it may guarantee less legal protection than a domestic partner.
Key features and how it achieves sovereignty
- Isolated infrastructure: A hyperscaler builds dedicated data centers within the target territory. Those are physically and logically separated from the provider’s global commercial cloud infrastructure.
- Local operations: The infrastructure is managed and operated by a local workforce, often under the hyperscaler’s separate legal entity registered within the country.
- Controlled access: Strict access controls and policies are in place to prevent non-local employees from accessing any part of the sovereign cloud.
- Technology and services: Customers can access global hyperscalers’ advanced services and innovations while adhering to local sovereignty requirements.
Best suited for: Organizations that handle less sensitive data while still having stringent compliance needs.
Top players in the cloud market have already started responding to sovereignty demands with dedicated offerings. These include:
- AWS European Sovereign Cloud: A separate Europe-based AWS region operated independently from existing AWS entities and staffed only by EU personnel.
- Microsoft Sovereign Cloud: Azure sovereign cloud environments (such as AzureChinaCloud and AzureUSGovernment) and sovereign offerings across Europe, providing data residency, compliance, and localized operations.
- Google Sovereign Cloud: A cloud delivered in collaboration with European partners, giving customers control over operations and encryption key management.
3. The hybrid sovereign model
The hybrid model is a flexible configuration combining a sovereign environment (either local or hyperscaler-based) with other standard private or public clouds. Organizations use the hybrid model to strategically distribute their workloads based on sensitivity.
Key features and how it achieves sovereignty
- Sensitive data: Highly regulated and sensitive data is stored and processed in the sovereign portion of the architecture to ensure compliance and security.
- Less sensitive workloads: Less critical applications and data run on a standard public cloud to utilize its global reach and cost-effectiveness.
- Interconnectivity: Secure network connections between the cloud environments enable data exchange when necessary.
Best suited for: Organizations that need to balance strict cloud sovereignty requirements with the flexibility of different cloud models. This approach is common for large enterprises with diverse data categories and application needs.
Design an effective hybrid cloud strategy—follow our expert guide!


Success!

Each model provides a pathway to different levels of digital sovereignty and ensures your sensitive data remains secure. The choice between them depends on where you operate, what you need to protect, and how much control you require. To make the right call, assess your regulatory obligations, risk tolerance, and technological requirements.
Key factors and tips for successful sovereign cloud implementation
Extensive preparation is half the job when it comes to building a sovereign environment in the cloud. Before embarking on this journey, our experts recommend taking several steps across the following key areas:
Regulations and compliance
- Understand the “why”: Clearly identify which regulations drive your need for cloud sovereignty. This could be the EU’s GDPR, the implications of the Schrems II ruling (impacting data transfers between the EU and the US), or specific national laws governing critical industry data.
- Go beyond data residency: In most cases, compliance demands more than limiting where data can be stored. Consider which laws govern the data (data sovereignty) and who is authorized to access it (operational sovereignty).
- Engage legal and compliance teams: Getting consistent legal counsel is crucial before using new cloud platforms or third-party services. It helps validate that a provider’s offering meets legal requirements and mitigates the risks tied to data access laws like the US CLOUD Act.
Data classification and application scoping
- Classify your data: Conduct a comprehensive audit to classify your data based on its sensitivity and the regulatory requirements attached to it. Some workloads may be suitable for residing outside the sovereign environment.
- Classify your applications: Determine which applications process, store, or transmit sensitive data. This will define the scope of the migration and help create an optimized strategy.
Total cost of ownership (TCO)
- Prepare for larger expenses: Sovereign environments often cost more than standard public clouds. They are associated with specialized infrastructure, limited scaling, and higher operational overhead.
- Factor in all costs: Your TCO calculation should include not only the provider’s fees but also the costs of migration, application refactoring, and the skills required to manage the new environment.
While larger expenses may seem initially off-putting, N-iX Chief Technology Officer explains it is a worthy investment.
Sovereign cloud decisions made with long-term strategy in mind shape how much control your business keeps over its data and operations. A well-designed sovereign architecture strengthens your position in regions where security and legal control are non-negotiable. It can open access to new markets and reduce the risk of costly regulatory setbacks.
Read more and learn how to keep your cloud costs in check
Provider due diligence
- Assess sovereignty claims: Investigate potential vendors to understand how they achieve sovereignty. For global providers, this means assessing the operational and legal separation of their sovereign offering. For local providers, it means evaluating their technical capabilities and resilience.
- Assess relevant functionality: Some sovereign environments, particularly newer ones, may offer a limited range of services compared to the same provider’s global public cloud. Ensure the services you need (e.g., specific databases, AI/ML tools, or security services) are available and mature.
- Evaluate the ecosystem: A strong strategy requires a robust ecosystem for migration, security, and management. Look for a provider with a network of local partners who can support your long-term growth.
Security and encryption
- Control your keys: A critical aspect of technical sovereignty is controlling your encryption keys. Evaluate your chosen provider’s key management services (KMS) and consider a “Hold Your Own Key” (HYOK) or “Bring Your Own Key” (BYOK) strategy to ensure only your organization can decrypt its associated data.
- Tailor your security to a sovereign environment: Implement robust identity and access management (IAM), network security, and continuous monitoring.
Scaling and extended functionality
- Consider scalability limitations: Sovereign environments are purposefully disconnected from public cloud resources. This means that your global scalability potential would be limited to other sovereign clouds within the same geographic and legal boundaries.
- Evaluate available functionality against your needs: Smaller providers may offer reduced functionality compared to the services offered by hyperscalers. Consider the adjustments you may need to make to adapt your current systems to new providers.
Exit strategy and avoiding vendor lock-in
- Plan for the future: Before committing to a provider, have a clear understanding of what it would take to migrate your workloads to another platform if necessary. Prioritize solutions that use open standards and facilitate data portability.
The future of sovereign clouds
Cloud sovereignty is no longer a niche concern. As international data protection regulations multiply, more organizations are rethinking how and where they manage sensitive data.
Over time, today’s digital sovereignty market will shift toward more consistent frameworks. As these cloud offerings mature, businesses will no longer have to choose between strict controls and innovation. For many organizations, sovereignty will evolve from a compliance necessity into a strategic asset.
Still, the current landscape is complex. Designing an effective sovereign strategy requires diverse domain expertise and careful planning. A trusted cloud partner can help align your infrastructure with sovereignty goals while preserving the critical functionality your business relies on.
Here’s how N-iX can help you build a robust sovereign cloud
With over 23 years of experience, N-iX helps organizations across finance, healthcare, energy, and other highly regulated industries meet evolving cloud requirements. We partner with top hyperscalers, including AWS, Microsoft, and Google, to bring you proven expertise in building secure, compliant cloud solutions at scale. Being a global technology company, we specialize in designing architectures that meet even the most rigorous sovereignty standards.
Our team includes over 400 experienced cloud engineers and 180 certified cloud experts to assist you with the following:
- Navigating regulatory complexity: We help align your cloud architecture with local and international laws and resolve conflicts between overlapping regulations.
- Providing implementation and managed services with local expertise: With a vast talent pool across 25 countries, we offer engineering and consulting services tailored to your regional regulations and business needs.
- Designing fit-for-purpose applications: Our cloud engineers build scalable solutions that balance sovereignty, performance, and cost.
- Ensuring auditability and compliance readiness: We help you build transparent, auditable environments ready to withstand legal scrutiny and security reviews.
- Integrating with legacy systems or multi-cloud setups: We ensure seamless interoperability and consistency across diverse infrastructures.
Whether you are evaluating sovereignty options or already planning your next migration, N-iX is ready to help you confidently design and implement a resilient solution.
References
1. How to Evaluate Sovereign Hosting Options to Reduce Geopolitical Risk. Gartner
Have a question?
Speak to an expert