Organizations worldwide are trying to stay ahead of evolving regulatory demands while keeping control over their most sensitive systems. New rules, cross-border data conflicts, and rising security expectations are forcing businesses to rethink how they operate and store data. On top of that, conflicting laws can often complicate their modernization efforts.
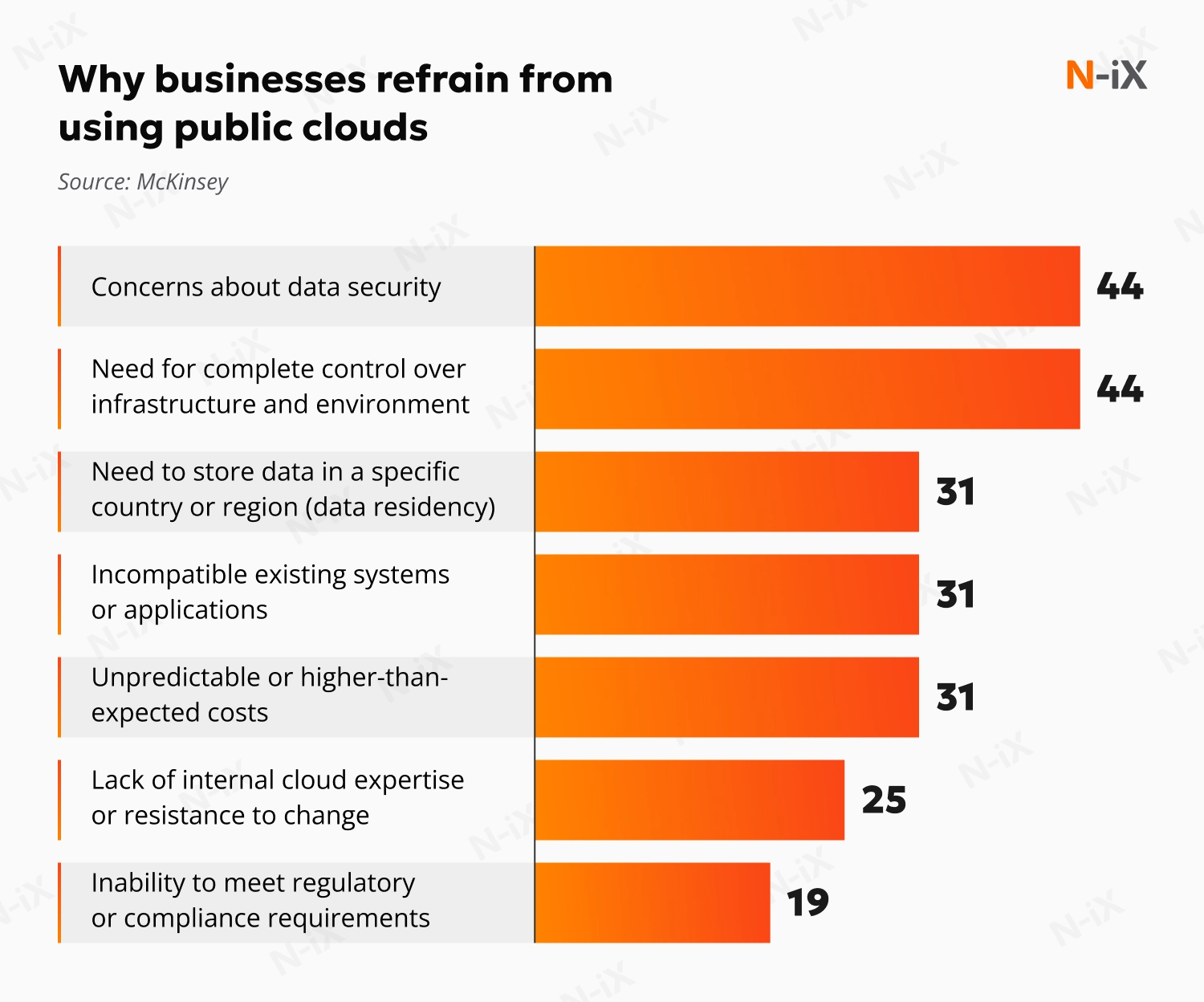
To address the growing pressure, many companies are seeking stronger control over their technology, infrastructure, and data handling. EU digital sovereignty is the concept they turn to when reassessing cloud strategies and operational decisions. This shift is reflected in a McKinsey survey of European companies that do not use public clouds. Nearly half the respondents cite security and infrastructure control as their main concerns. In fact, four of the top seven barriers to public cloud adoption relate directly to issues that sovereignty initiatives address. The graph below outlines these reasons in detail.
The aspiration is clear. Enterprises want the advantages of modern cloud platforms, but they need confidence that their systems and data remain protected under European regulations. That leaves a pressing question: how can you stay competitive without sacrificing compliance and control? Sovereignty offers a way to bridge that gap.
In this article, we’ll untangle what comprehensive sovereignty means, why it’s becoming essential for compliance, and, most importantly, how your business can achieve it.
What is digital sovereignty?
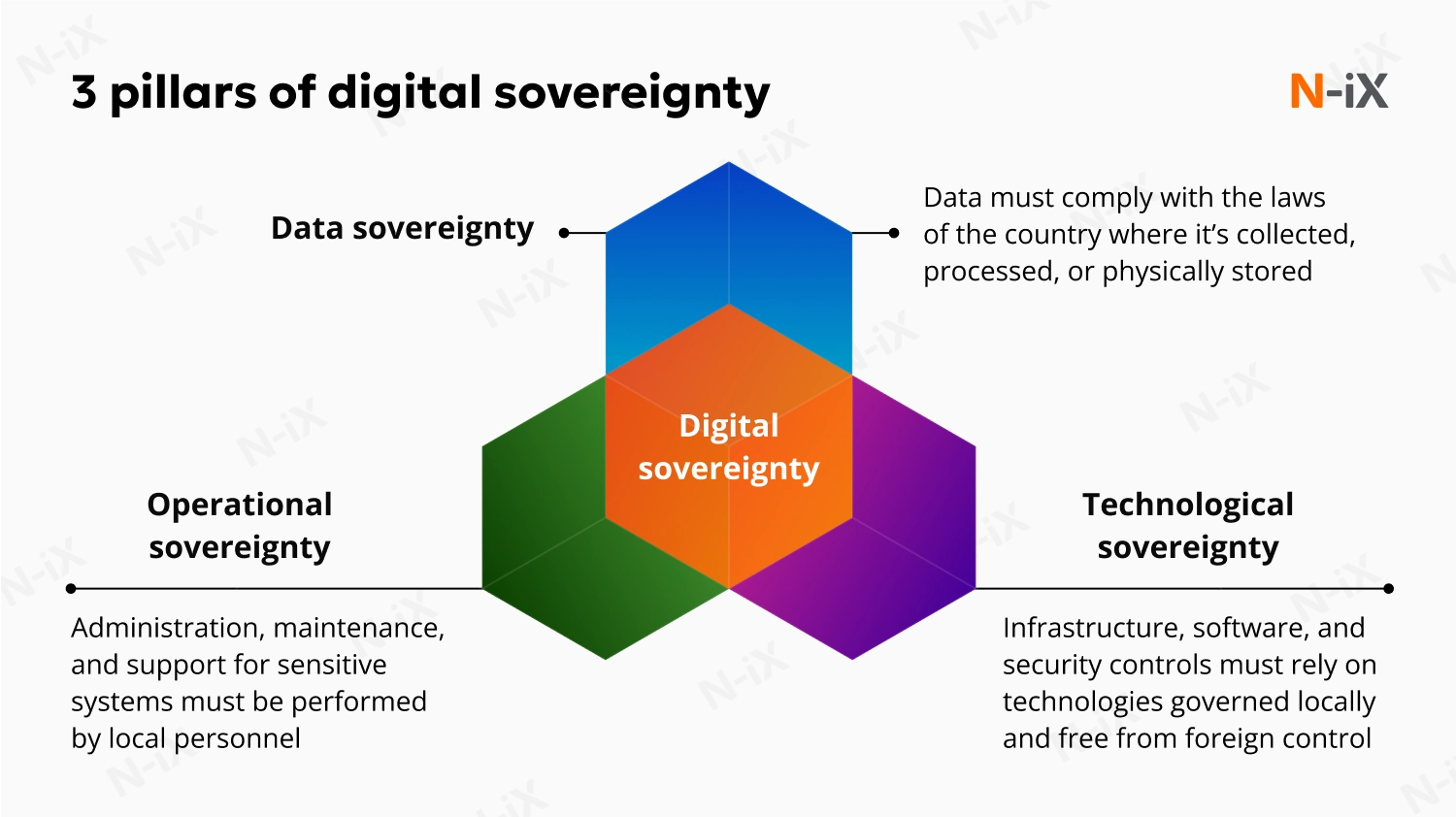
Digital sovereignty describes a country’s or organization’s ability to control its data, infrastructure, and operations within its own jurisdiction, with no external influence. According to the European Parliament, it defines a nation’s ability to “act independently in the digital world.” [1] Fundamentally, it outlines the capacity to apply one’s own rules to technology, cloud services, and information flows.
This broader idea is built on the following layers of control that determine who stores, processes, manages, and can legally access digital assets:
- Data residency refers only to the physical location where data is stored or processed (e.g., servers in Germany). Placing workloads on servers within specific countries is often required, but location alone doesn’t guarantee full legal protection.
- Data localization is a policy that mandates that specific data categories remain within national borders, often for regulatory or security reasons.
- Data sovereignty establishes which jurisdiction’s laws apply to the data throughout its lifecycle. Even if the data is hosted abroad, it still must comply with the legal framework of the country where it originates or is processed.
- Operational sovereignty ensures that administration, maintenance, and support for sensitive systems are performed by personnel subject to local authority. This condition prevents foreign teams or vendors from having the technical ability to access restricted environments.
- Technological sovereignty relies on customer-controlled encryption and cryptographic key management. This includes models like Hold Your Own Key (HYOK) or Bring Your Own Key (BYOK), where encryption keys remain fully under the customer’s control. These guardrails keep service providers and foreign governments from accessing data without explicit permission.
Understanding what sovereignty requires in theory is a starting point. But how do you actually translate these principles into daily technological and operational decisions? Anton Xuereb, our Solutions Architect, emphasizes that achieving complete autonomy requires deliberate design choices and infrastructure management that put control in your organization’s hands.
To simply “follow the rules” is an overwhelming piece of advice. Practically, companies need to know how to structure their systems and operations so they can truly control their data and infrastructure. Real autonomy comes from combining compliance with optimized, locally managed solutions.
What does it take to achieve EU digital sovereignty? 6 key tips
Digital sovereignty in Europe becomes manageable once you break big regulatory ideas down into clear, actionable steps. Here are the essentials that can help you move from intention to execution.
1. Build a sovereign cloud infrastructure
A sovereign cloud is a strategic computing environment that helps organizations meet sovereignty requirements while retaining the flexibility and scalability of cloud services. The key is choosing an approach that fits your regulatory exposure and the desired level of operational risk management. Three main options include:
-
Hyperscaler partnership model
Global cloud providers develop dedicated cloud regions that are physically and logically separated within the target country. The AWS European Sovereign Cloud, for instance, launched its first region in Germany in early 2026. It operates under EU law with EU-based personnel managing operations and support. This model provides access to advanced services, including AI/ML tools, while meeting strict sovereignty requirements.
Tip from N-iX: While sovereign offerings from US hyperscalers reduce risk, they do not fully eliminate exposure to the US CLOUD Act and similar extraterritorial legislation. Factor this into your sovereignty assessment and define additional technical, contractual, or architectural safeguards where required.
-
Local provider model
This model relies on cloud platforms built and operated by EU-native companies, such as OVHcloud, Hetzner, and Scaleway. It offers the highest level of protection from foreign influence as the provider is governed exclusively by local legislation.
-
Hybrid sovereign model
When adopting this approach, you can allocate workloads across different environments, based on their sensitivity. Highly regulated or mission-critical data stays within a sovereign environment, while less sensitive applications run on standard public clouds to maximize efficiency. This model is the most suitable one for organizations that need strong European digital sovereignty but still want flexibility.
Choose the right EU sovereign cloud provider—get the report!


Success!

2. Control your encryption keys
Implement technical safeguards like HYOK or BYOK models. This approach ensures that your organization retains custody of encryption keys, preventing cloud providers or foreign governments from independently accessing your data. To support stronger sovereignty in digital infrastructure, you can use external key management services (KMS) to keep encryption keys outside the cloud vendor’s control.
3. Use European-built software and end-to-end encryption
Enterprises can reduce exposure to foreign surveillance laws by choosing tools developed and hosted in Europe. Beyond that, our experts recommend using platforms that secure communications, files, and metadata with end-to-end encryption. Pair this with zero-trust architecture principles supported by strong identity and access management and role-based controls to limit who can access sensitive data.
4. Conduct data classification and ensure data sovereignty
Conduct a comprehensive audit to classify data by sensitivity (for instance, personal, financial, and IP) and the specific regulatory requirements attached to it. This mapping determines which workloads require the full isolation of a sovereign environment. Strengthening data residency at this stage is an effective way to support EU digital sovereignty. This step helps you decide where data should physically reside, which providers can host it, and how to enforce location-based policies.
Read more to discover how data sovereignty supports compliance
5. Ensure regulatory readiness and logging
Digital sovereignty in the EU is measured by your ability to produce clear, regulator-ready evidence on demand. Develop policies to maintain immutable, time-synced logs for administrative actions, data access, and configuration changes to create the required audit trails. This operational transparency is essential for compliance frameworks like DORA.
6. Develop an exit strategy
An exit strategy should be designed at enterprise level, not improvised during a crisis. Your cloud principles and guidelines need to set clear parameters upfront. This includes how quickly you must be able to exit a region or cloud provider, and whether the target migration environment is another cloud, on-premises infrastructure, or both. These decisions directly influence architecture rules, platform choices, and operational constraints, so they must be agreed on before large-scale adoption begins.
Due diligence should then translate these principles into practical planning. This means understanding which technical and business dependencies are introduced during cloud migration or cloud-native development. Costs, timelines, and risks of moving away from specific services should also be estimated and documented. To reduce the risk of vendor lock-in, prioritize solutions that use open standards to facilitate solution and data portability.
Applied together, these practices enable organizations to meet the growing requirements for control and compliance. And the pace of this change shows no signs of slowing. N-iX Chief Technology Officer Valentyn Kropov notes that with new rules emerging across the world, sovereignty “will become a priority for businesses sooner rather than later.”
Digital sovereignty is becoming a decisive factor for operating in Europe. Companies that align their systems and operations with sovereignty requirements strengthen compliance and competitiveness. Meanwhile, those who rely on non-sovereign architectures face growing constraints, regulatory conflicts, and increased exposure to threats.
So, what laws are driving this shift toward greater digital independence, and where do they have the strongest impact on global companies? Let’s take a look.
Regulations driving EU digital sovereignty
GDPR vs. US CLOUD Act
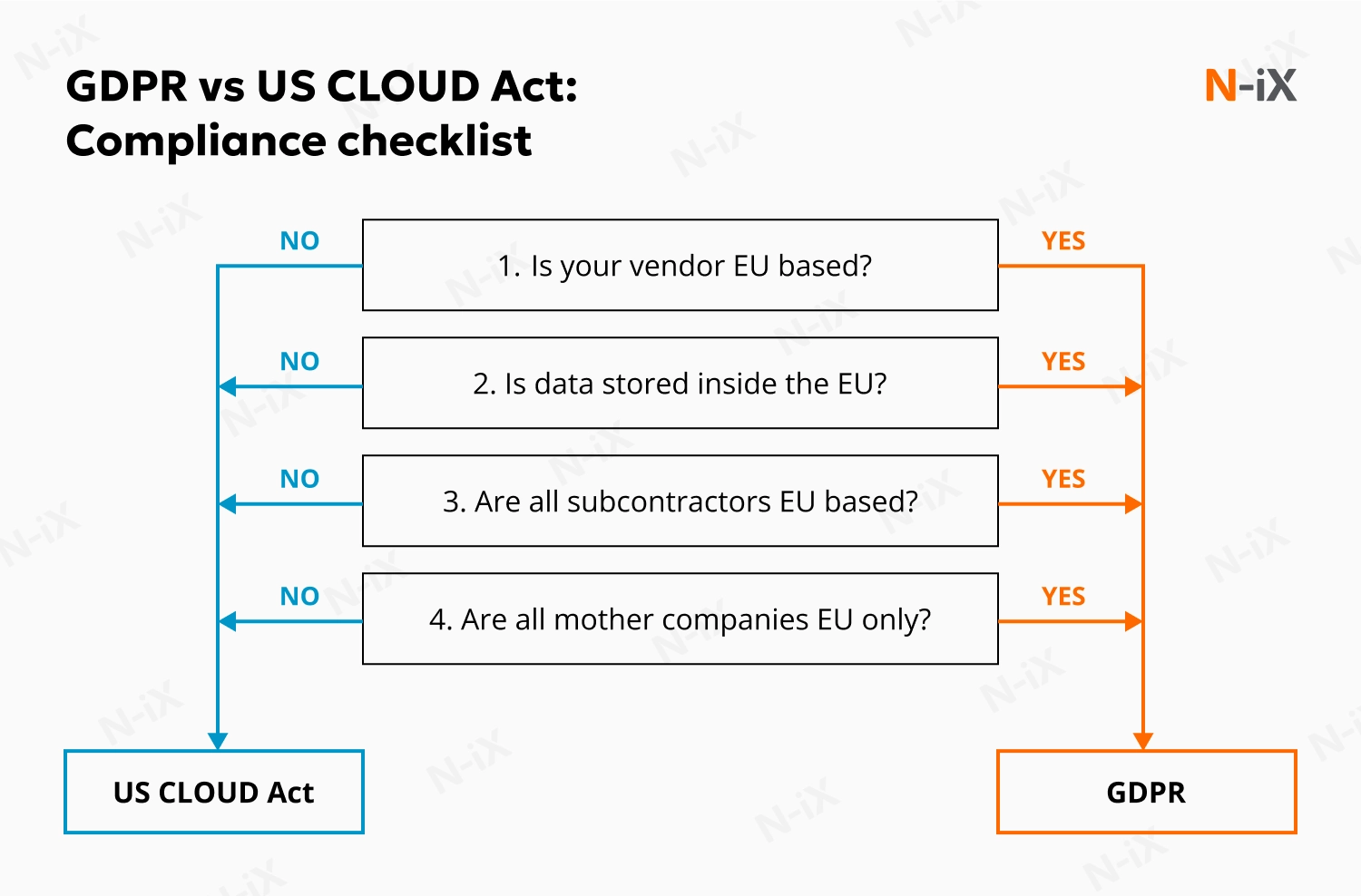
The General Data Protection Regulation treats the protection of personal data as a fundamental right and imposes strict conditions on cross-border transfers. Following the Schrems II ruling, companies must also demonstrate that any international data flow maintains EU-level safeguards, which has substantially raised the bar for achieving compliance.
The picture becomes more complicated when set against the US CLOUD Act. This law allows American authorities to compel US-based service providers to disclose customer data even if it is stored in another country. Following its enactment in 2018, the act was tested almost immediately: in United States v. Microsoft Corp., prosecutors sought access to emails stored in Microsoft’s Dublin datacenter. [2] Microsoft ultimately had to comply. Although the case focused on a particular criminal investigation, it set a larger precedent for global businesses. It became evident that foreign-hosted data may still fall within the reach of US law.
For most enterprises, complying with both GDPR and the CLOUD Act means navigating rough regulatory waters. Concerns about conflicting obligations grow, especially as enforcement under GDPR accelerates. In 2023, Meta received a record-breaking €1.2B (approximately $1.4B) fine for transferring personal data to the US based on standard contractual clauses. [3] The corporation was also ordered to bring its practices into full compliance with the GDPR. For many companies, it was a clear reminder that even long-standing mechanisms for transfers face newly intense scrutiny.
These tensions have pushed digital sovereignty in Europe from a technical matter into a legal and strategic one. As jurisdictions assert more control over how and where data is handled, businesses must reassess their regulatory exposure.
Digital Operational Resilience Act (DORA)
Effective January 2025, DORA is an EU regulation introduced to strengthen the digital resilience of financial entities. It applies to banks, insurers, investment firms, and critical third-party information and communications technology (ICT) providers. DORA requires institutions to prove that their digital operations and ICT systems are resilient, auditable, and accessible to regulators.
As it stands, compliance becomes complex when organizations rely on cloud services from non-EU providers. Without EU digital sovereignty, foreign laws, such as the US CLOUD Act, can authorize data disclosure that bypasses EU oversight. This interference creates a direct risk to the resilience and auditability that DORA requires.
As a result, many organizations are turning to sovereign cloud models to ensure continuous auditability and compliance. According to Gartner, as many as 60% of non-US financial services firms will adopt sovereign clouds by 2028. [4]
NIS2 Directive
Entering enforcement through 2025, NIS2 extends cybersecurity obligations for digital sovereignty in the EU to a spectrum of critical sectors, including energy, transport, healthcare, and digital infrastructure. The directive mandates rigorous risk management and fast incident response while giving national authorities stronger oversight of security processes. It applies to two groups: essential entities (such as large operators in critical sectors) and important entities (typically midsize organizations or those supporting critical supply chains).
Sovereignty matters because NIS2 demands EU-level visibility into the systems that underpin these services. Using sovereign solutions helps organizations ensure that sensitive operational data, monitoring, and security controls remain within EU jurisdiction. This is key to meeting the directive’s resilience and supply chain security requirements, particularly by reducing dependence on non-EU ICT providers.
EU Data Act and EU AI Act
The EU Data Act, applicable from 2025, is a significant component of the EU’s sovereignty framework. In contrast to GDPR, which prioritizes protecting personal data and privacy, the Data Act focuses on non-personal and industrial data. In the context of sovereignty, the act prohibits unlawful third-country access to non-personal data stored or processed in the EU. This underscores that the EU’s sovereignty efforts extend beyond individual privacy to strategic, industrial, and operational datasets.
The EU AI Act complements this approach by extending sovereignty principles from data to AI systems. The AI Act introduces requirements around transparency, risk management, and human oversight for AI systems operating in the EU. Together, the Data Act and the AI Act reinforce the need for organizations to maintain technical and operational control not only over data, but also over how AI systems are trained, deployed, and governed.
Sovereignty, in the context of both acts, helps companies avoid penalties and maintain business continuity. Adopting sovereign infrastructures ensures operational autonomy and technical controls, such as customer-managed encryption, while supporting regulatory readiness and auditability.
How N-iX supports your next steps toward EU digital sovereignty
Sovereignty is becoming crucial as regulations tighten, expectations rise, and organizations face growing pressure to prove sufficient control over their digital assets. Meeting all these demands requires a strategy that can withstand regulatory shifts without significantly impeding your innovation potential. At one point, business leaders face a simple but critical question: what should your teams actually do next? By partnering with a technology provider like N-iX, you can answer it confidently.
N-iX helps enterprises across finance, healthcare, energy, and other regulated sectors navigate complex sovereignty requirements. We build secure cloud architectures, implement effective governance practices, and embed controls that support long-term resilience and modernization.
With a team of 2,400 tech professionals, 23 years of experience, and partnerships with leading hyperscalers, we are fully prepared to help your organization grow with confidence.
References
1. Digital sovereignty for Europe—European Parliament
2. United States v. Microsoft Corp., 584 U.S. (2018)—US Supreme Court Center
3. 1.2 billion euro fine for Facebook as a result of EDPB binding decision—European Data Protection Board
4. Quick Answer: Sovereign Cloud Implications for Financial Services CIOs—Gartner
Frequently Asked Questions
1. How is digital sovereignty achieved?
Comprehensive sovereignty is achieved by ensuring control across several layers: data (full authority over how and where data is accessed), operations (independent management of critical systems and processes), and clouds (use of infrastructure that is legally and physically protected from foreign jurisdiction).
2. Why is the US CLOUD Act a threat to EU digital sovereignty?
The CLOUD Act authorizes US authorities to compel US-based providers to disclose data held anywhere in the world. This conflicts directly with the GDPR, which restricts cross-border data transfers unless specific conditions are met. This extraterritorial reach undermines EU legal control.
3. What is the difference between data residency and digital sovereignty?
Data residency only refers to the physical location of data storage. Sovereignty is the broader ability to control technology, infrastructure, and data without reliance on external entities. Residency alone does not guarantee legal protection from foreign laws like the US CLOUD Act.
4. Which sectors are most affected by the new EU regulations?
Highly regulated sectors like finance, healthcare, and critical infrastructure face the strictest requirements. DORA applies specifically to financial entities, mandating operational resilience and auditability. NIS2 extends cybersecurity obligations across critical infrastructure and supply chains.
5. What risks do enterprises operating in the EU face without sovereignty?
Without European digital sovereignty, enterprises risk exposure to foreign laws like the US CLOUD Act, potential GDPR violations, and unmitigated supply chain vulnerabilities. They may lose control over sensitive data, face operational disruptions from external actors, and encounter regulatory penalties if infrastructure or service providers fall outside EU legal protections.
Have a question?
Speak to an expert