According to IBM’s Cost of a Data Breach Report, unpatched vulnerabilities, stolen credentials, and system errors can cost enterprises anywhere from $4M to $5M in damages per breach. To discover and remedy such weaknesses before they can be exploited, businesses turn to penetration testing. But even the most comprehensive testing efforts can be ineffective or even damaging without a structured approach. This is where penetration testing methodologies come in. They bring consistency and safety to the process, aligning assessments with real business risks, compliance goals, and long-term security improvements.
So, which methodologies can best support your security objectives? Read on to explore the top frameworks, when to apply each, and how to create a methodology-driven pen-testing roadmap.

4 penetration testing methodologies with use cases
Imagine assuming the role of an assessor who attempts to get through your system’s security. Where do you start? How do you ensure the process is time-efficient and doesn’t cause major disruptions? And, no less importantly, how should you document discoveries and assert that no known vulnerabilities were missed?
An experienced security consultant with a deep understanding of effective penetration testing methodologies and standards can confidently answer these questions. Pen testing specialists can also select the most appropriate framework for your needs: some offer step-by-step instructions, while others focus on technical requirements. Our experts highlight the following top methodologies based on their practical relevance:
1. The OWASP penetration testing toolkit
Open Web Application Security Project (OWASP) is a non-profit organization with a mission of helping others improve their web application security. It’s renowned for the OWASP Top 10—a comprehensive and well-maintained list of key vulnerabilities in web security, often used as a reference point during web application security testing. While not a methodology, the list helps organizations prioritize threats based on exploitation method, potential impact, and difficulty of detection.
Another contribution of this foundation, the OWASP Testing Guide (OTG), offers a more comprehensive approach. It describes the four main phases of penetration testing and outlines eight key principles to follow when preparing for, conducting, or analyzing the test. The guide also provides testing methodologies for specific aspects being evaluated, such as session management, input validation, identity management, authentication, and so on.
Besides the OTG itself, OWASP provides several related methodologies dedicated to particular testing domains, including the Web Security Testing Guide (WSTG), the Mobile Application Security Testing Guide (MASTG), and the Application Security Verification Standard (ASVS).
Who needs the OWASP Testing Guide?
Being exclusively focused on web applications, the OTG is a useful framework for all businesses that prioritize their online services, customer data, and user interactions. In particular, it may be the best choice if you represent:
- An enterprise with extensive web architecture and customer-facing applications, such as an ecommerce platform;
- A financial organization offering online banking services;
- A mobile app developer (following the Mobile Application Security Testing Guide);
- A software as a service (SaaS) provider focused on building secure web applications.

2. Penetration testing execution standard (PTES)
Developed in 2009, the PTES methodology is one of the most recent frameworks, but it’s also widely regarded as one of the most comprehensive. It aims to provide a detailed, organized guide, equipping organizations with consistent and repeatable steps to conduct a pen test. The PTES covers the entire process, outlining seven key phases, from pre-engagement to post-exploitation and reporting. While it doesn’t offer technical guidance on how to carry out a specific test, the PTES is flexible and easily adaptable to diverse needs.
When do you need the PTES?
The PTES applies to network, web, social engineering, and even physical pen testing. It’s versatile and works well with many penetration testing techniques while staying consistent. Consider using the PTES when you need to:
- Standardize your testing efforts across different assessment providers;
- Build an internal security testing program from scratch;
- Meet regulatory requirements, especially if your industry (such as finance, healthcare, or insurance) is subject to rigorous compliance reporting;
- Conduct penetration testing across complex environments (for instance, when assessing both network security and staff’s susceptibility to social engineering attacks).

3. Open Source Security Testing Methodology Manual (OSSTMM)
First developed in 2001 as a security best practices collection, the OSSTMM quickly grew into a solid and complete methodology. It’s published by the Institute for Security and Open Methodologies (ISECOM) and peer-reviewed to ensure continuous improvement and accuracy. This framework brings a new perspective to penetration testing by encouraging a scientific approach—using quantitative metrics instead of simple “pass” or “fail” results.
Additionally, the OSSTMM spotlights operational security as part of a comprehensive approach. While, initially, it focused on network protection, the latest edition extensively covers operational processes, human factors, telecommunications, wireless connections, and physical security.
When do you need to use OSSTMM?
The OSSTMM is a particularly useful pen-testing framework for cybersecurity compliance auditing and testing across multiple operational areas. Consider applying OSSTMM when you need to:
- Prepare for compliance audits aligned with ISO 27001, PCI DSS, and other standards (the methodology offers specific test cases to facilitate the process);
- Assess non-digital components, such as human factors and physical access restrictions;
- Demonstrate due diligence to regulators, partners, or internal stakeholders.

4. NIST Special Publication 800-115
The NIST Special Publication (SP) 800-115 is among the most technical and instructive penetration testing methodologies. It is developed and maintained by the National Institute of Standards and Technology, a US federal agency that outlines standards for various fields, including cybersecurity.
Unlike the OSSTMM, which offers a broader operational view, the NIST 800-115 focuses on network and IT infrastructure security, as well as the technical side of pen testing. It methodically covers penetration testing best practices for each aspect of the evaluation, including planning, discovery, attacking, reporting, and the testing team’s skills assessment.
Who needs the NIST SP 800-115?
The NIST 800-115 is designed for government agencies whose testing efforts must align with the corresponding standards. It’s also effective for those looking to establish a continuous, formalized penetration testing process, including:
- Organizations that follow federal standards, such as healthcare or financial institutions;
- Teams conducting infrastructure-focused penetration testing, especially involving networks, cloud-based systems, and endpoints;
- Enterprises that need clear technical guidance to establish or revise their security assessment procedures.

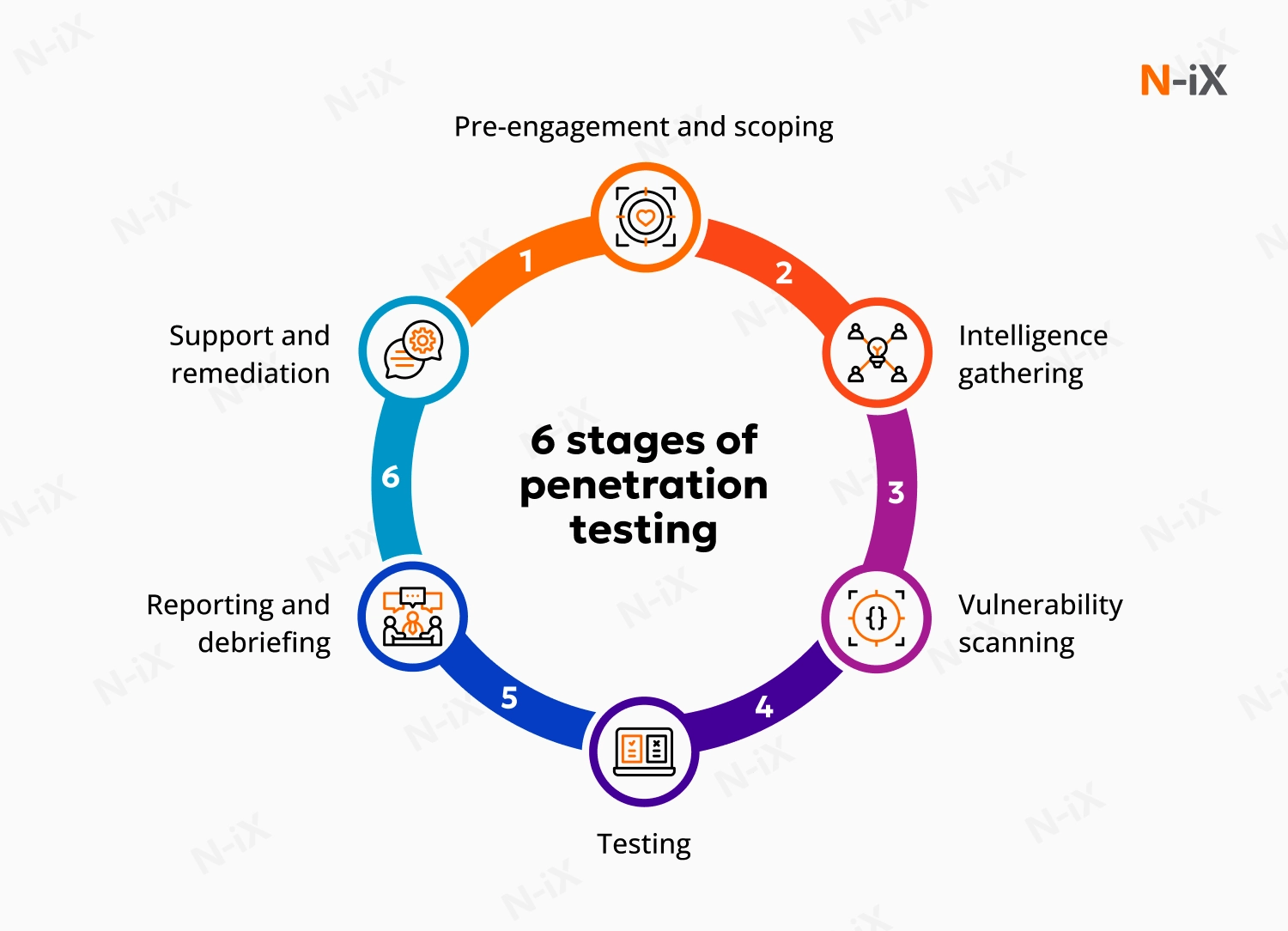
How penetration testing is conducted: 6 key stages
Penetration testing methodologies vary in structure, outlining different testing stages and techniques. Moreover, the final roadmap for the assessment also depends on your business objectives and the scope of assets to test. At N-iX, we tailor the assessment to your specific needs and chosen frameworks, but several core stages remain consistent across all methodologies. Let’s explore our experts’ approach phase by phase.
1. Pre-engagement and scoping
Before starting the assessment, we work with your teams to determine the scope and goals of the test. This stage helps us define what will be tested, which methods to use, and what constraints will be in place. Several steps we take during this phase include:
- Discussing your objectives: This helps align the test with specific business risks, ensuring we focus on real-world attack scenarios, not just technical gaps.
- Inventorizing assets, applications, and systems: We map all components to be assessed, as well as their dependencies.
- Determining the approach: Depending on your requirements, we may opt for different types of penetration testing like black box, white box, or gray box. These methods vary by the pen tester’s amount of prior knowledge about the systems.
- Deciding on the level of access: We also determine whether the assessment will be internal or external. During internal pen tests, assessors mimic malicious insiders, while external tests simulate attacks from the outside.
- Outlining legal and operational boundaries: We clearly define the rules of engagement, such as what systems are off-limits and when we can commence testing to minimize operational disruptions.
Many pen-testing methodologies, such as the PTES, stress thorough pre-engagement to ensure clarity, establish mutual expectations, and define legal boundaries before any testing begins.
2. Intelligence gathering
Once the scope is defined, our team conducts reconnaissance to collect as much information about the target systems as possible. Methodologies like the OSSTMM and PTES divide this stage into passive and active intelligence gathering. We apply both approaches to study your system architecture, network components, and services thoroughly.
For instance, we may analyze public sources (such as the ICANN registry) for domain records as a form of passive reconnaissance, or we can interact with live systems to map open ports, taking the active approach.
3. Vulnerability scanning and analysis
Before simulating offensive tactics, we perform a vulnerability assessment using automated tools to identify known weaknesses across your systems. We also analyze the discovered vulnerabilities to determine how damaging they can be to your business if exploited. This helps prioritize threats and guides our approach in the next stage: controlled exploitation.
Strengthen your cloud security with proven best practices—get the guide now!


Success!

4. Testing
With guidance from the selected penetration testing methodologies, our experts conduct controlled exploitation using manual and automated techniques. We simulate advanced attack scenarios according to the parameters of the test to assess how successful a real attacker might be. While we extensively test the risks identified during vulnerability scanning, this stage also covers social engineering attacks and other threats not caught by scanning tools.
Read also: Penetration testing vs vulnerability scanning
5. Reporting and debriefing
After completing the testing stage, we detail our findings in a comprehensive report. It includes the discovered vulnerabilities, their severity, and potential impacts—along with steps to reproduce each issue. Our experts also list applicable fixes and recommendations for strengthening your security posture. Clear documentation is one of the core penetration testing best practices, helping teams prioritize remediation effectively, meet compliance requirements, and maintain a record for future testing.
6. Support and remediation
While reporting is a crucial stage of the penetration testing process, at N-iX, it’s not necessarily the final one. We can assist you with remediation efforts, verify fixes through additional testing, and help build a regular assessment cycle. Continuous testing and vulnerability management, emphasized in methodologies like the OSSTMM, help you reinforce defenses and maintain compliance over time.
Wrapping up
Pen testing is most effective when grounded in structured penetration testing methodologies. These frameworks help ensure tests are consistent, focused, and aligned with real-world risks. However, effectively applying any methodology takes expertise.
To maximize the value of your testing efforts, it’s crucial to work with security professionals who understand both the methodologies and your unique environment. By outsourcing penetration testing to the right partner, businesses gain more accurate insights, ensure compliance, and build more resilient, high-performing systems.
Why should you trust N-iX to improve your enterprise security?
- N-iX is a trusted tech services provider with 23 years of experience in the international market.
- We have completed over 100 penetration testing, vulnerability management, and risk assessment projects, establishing long-lasting security for businesses across 22 industries.
- Our seasoned team consists of over 2,400 engineers, cybersecurity specialists, and cloud experts, successfully delivering projects for more than 160 clients.
- N-iX maintains compliance with ISO 27001, GDPR, CyberGRX, FSQS, SOC 2, PCI DSS, and other top industry standards to ensure we conduct security assessments safely and effectively.
Have a question?
Speak to an expert



