There is a myth that moving to the cloud means sacrificing security. And it needs to be debunked. According to Gartner, by 2021, public cloud infrastructure workloads will have 60% fewer security incidents than traditional data centers. But the belief that everything in the cloud is 100% protected is also a myth. There are a number of challenges businesses face with cloud technology security. And here we’ve highlighted several steps you need to take to mitigate security issues in cloud computing.
-
Accept a shared responsibility security model
It is important to understand that security in the cloud is a shared responsibility between you and your cloud provider. As data shows, top threats to data security come not from cloud providers but rather from business users, hackers, and IT staff.

The lion’s share of security obligations lies on the customer’s shoulders. The customer is not responsible for the security of physical hosts, networks, and data centers. But still, they bear responsibility for securing data in the cloud. It’s true, cloud computing vendors put a special emphasis on security. Mature cloud providers like AWS, Azure, and Google Cloud are constantly investing in security and offer their own set of advanced cloud technology security controls. But it is the responsibility of the customer to apply and manage those controls provided by the cloud vendor. And depending on the type of service (SaaS, PaaS, IaaS), the customer is also accountable for the reliability of applications, middleware, runtime, and OS.

-
Plan for security across heterogeneous environments
The heterogeneity of modern enterprise environments that include both on-premise data centers and diverse cloud platforms poses a number of security vulnerabilities. They may include cloud account compromises, data exposures, cryptojacking. etc. Using multiple clouds complicates the cloud technology security strategy. Among organizations that had at least one security incident during the preceding 12 months, the number of organizations that use multiple clouds is 20% larger than those that use a single public cloud (44% and 24%, respectively).
Those companies that host applications across hybrid environments also risk suffering cloud attacks if they fail to coordinate security policies across these environments. Before migrating to the cloud platform, you have to decide on your strategy (single cloud vs multicloud vs hybrid cloud) and elaborate the cloud technology security policy accordingly.
-
Back up your data
It is essential to configure the backup of data to be able to restore any missing files, if necessary. Anything from a power outage at a data center to a security breach may cause data loss. If you have backups of databases stored on a server or in the cloud, you can quickly restore all the data. Besides, it is necessary to perform regular checks of the backup to make sure it is valid and the data is consistent. Some cloud providers offer cost-effective storage services you can use for the backup. Amazon and Dropbox offer great storage options for Apple users. Linux users can make use of Nextcloud, OneDrive perfectly suits Windows users. All these solutions can give you more than enough free or cost-effective storage services. Their pricing plans differ depending on your business purposes.
-
Encrypt your data
Encryption is an important layer of cloud security in cybersecurity. It protects your data by encoding it when at rest and in transit. It is difficult to decipher such data without a decryption key that only a limited group of people should have access to. Although many cloud providers offer native cloud security controls such as data encryption, many companies neglect it. According to the recent Cloud Security Threat report, 80% of respondents don’t use encryption at all. Thus, encryption is the top measure companies now plan to take in order to strengthen cloud data security.

-
Leave sensitive data on-premises
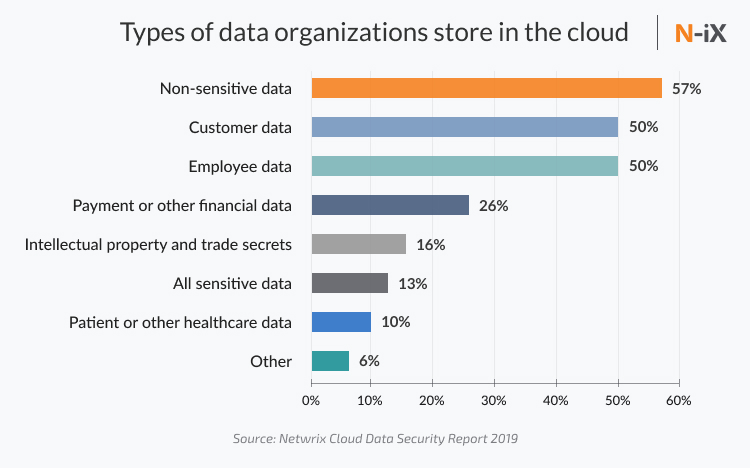
“21% of all files in the cloud contain sensitive data, up 17% over the past two years.” - Cloud Adoption and Risk Report 2019
Storing sensitive data in the cloud is still a common practice among some enterprises although they know that it is risky. Personally Identifiable Information (PII), personal healthcare information (PHI), financial data can not live in the cloud. This information is considered as sensitive and should be kept on-premises. Companies that operate sensitive data often opt for storing this data on physical data centers and use a public cloud platform for compute power, flexibility, connectivity, and scalability. Moreover, according to GDPR standards, healthcare and finance organizations are not allowed to store sensitive data on the public cloud platforms. They must keep the company’s critical data on physical servers in a particular region. Otherwise, they can be prosecuted.
-
Make use of automation
Most organizations haven’t leveraged automation for predicting and addressing cloud technology security issues yet. Without automation, however, it is almost impossible to protect your organization from cyberattacks, which become more and more sophisticated. Heading into the cloud-only future and looking to combine cloud services and security, companies need to master intelligent automation technologies such as RPA, Big Data, AI, IoT, etc. With the help of them, security teams can optimize their daily tasks, reduce response times to security events, simplify the investigation process, and minimize the damage from attacks.
Due to the lack of cloud technology security skills, interest in Security Orchestration, Automation and Response (SOAR) solutions is growing. According to Gartner’s report, 30% of organizations with a security team larger than five people will leverage SOAR tools in their security operations in 2020. This is 6 times larger than in 2019.
-
Adopt a DevSecOps approach
The complexity of cloud security configurations arises because security is not integrated throughout the whole development process. Today, companies need to make way for DevSecOps which incorporates security practices into every step of the agile development process. According to DevSecOps, each member of the development team is responsible for code security. Assessing security risks and fixing code is an integral part of the development process. By introducing security earlier in the life cycle of application development, it is possible to minimize security risks and increase app stability. Gartner predicts that DevSecOps will be embedded into 80% of rapid development teams by 2021.
-
Avoid Shadow IT
To be able to objectively assess the scope of Shadow IT and the risk it poses, first of all, companies need to admit that it does exist. The next step they should take is to figure out how fast their cloud portfolio is growing. There is a striking difference between the actual number of Shadow IT apps used within the organisation and what the IT and SecOps teams believe employees are using. According to the Cloud Security Threat Report, an average organization believes its employees are using 452 cloud apps. However, the actual number of Shadow IT apps in use per organization is nearly 1,807. Due to the lack of visibility into SaaS and IaaS, security teams can’t secure what they are not aware of.
To avoid shadow IT, companies need to make use of automation and tools such as a Data Loss Prevention (DLP) platform and a Cloud Access Security Broker (CASB). They will help gain greater visibility into their organization’s use of cloud services and security by discovering shadow IT applications and reporting on their risks. In addition, AI and machine-learning technology can help with the analysis of targeted attacks, enabling organizations to mitigate their harm.
-
Provide cloud security awareness training
Cloud security is not only about technology. It’s more about people and how they use this technology to combine cloud services and security. You need to ensure that the right technology is in the right hands. So the educated workforce is what matters the most.
It’s true, it is necessary to invest in cloud security tools like Cloud Access Security Brokers (CASB), Cloud Workload Protection (CWP), and Cloud Security Posture Management (CSPM) which help protect data, storage, and workloads from exposure or attack across IaaS, PaaS and SaaS. But what is more important is to train security teams on how to use them. According to the Cloud Security Threat Report, only 27% of organizations are confident in their ability to address all cloud security threats. 92% of respondents admit that they need to enhance cloud security skills. And 84% confirm they needed to add staff to close the gap.
Besides that, companies shouldn’t forget to regularly educate all employees on some basic security rules such as:
- Update passwords;
- Don’t use one password for all tools;
- Update anti-virus software;
- Don’t open susceptive links;
- Upgrade software to the latest installation.
The cybersecurity skills gap is indeed a serious problem. Thus, businesses find it helpful to partner with experienced service providers to prevent risks of cloud security in cybersecurity. N-iX is a reliable software development company with more than 18 years of experience on the market. We have a strong portfolio of cloud migration projects across a variety of industries: telecom, fintech, healthcare, retail, and more. Our expertise in cloud computing includes on-premise-to-cloud migration, cloud-to-cloud migration as well as multicloud and hybrid cloud management. Our experts have developed mature security practices that prove to be effective for many of our clients including Lebara, Orbus Software, FPL Online Pte Ltd, FinBursa.
Wrap-up
Cloud technology security is the hottest and most debated topic in the world of cloud computing. Today, in the face of the coronavirus outbreak, many companies from Wuhan to Silicon Valley are turning to cloud providers to ensure business continuity. But are they aware of possible security issues in cloud computing? With more people working from home, the number of cyberattacks grows as rapidly as cloud adoption. It becomes critical for organisations to build an effective cloud services security strategy. If you don’t know how to achieve maximum cloud security, contact our experts and they will be happy to help you.
Have a question?
Speak to an expert




